Technical notes for Cisco Certification Exam 100-105 ICND1
After my Cisco certification expired in December 2015, I decided to renew it again and this time aiming to get the full monty, the well-known, well-established CCNA certification. Starting with ICND1. Let's explore on this document the Technical notes for Cisco Certification Exam 100-105 ICND1 and some tips that I've used to pass the Cisco Certification Exam 100-105 ICND1, hopefully I'll get lucky... no, wait... luck does not exist on the Cisco world (or in the IT world for that matter): preparation and planning is the key. Let's do it!
Exam Code: 100-105 ICND1 http://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/100-105-icnd1.html
Update: The Cisco Certification Exam 100-105 ICND1 (Interconnecting Cisco Networking Devices) was retired 24th February 2020 https://www.cisco.com/c/en/us/training-events/training-certifications/certifications/entry/ccent.html#~stickynav=1 Nevertheless, the topics listed on this article are still very relevant
First of all, I would strongly recommend you to read the Cisco Technical Diaries that I created back on the day when doing my degree at West London University; I completed a Commercial System Management (Cisco) on my first year at the University. http://www.nazaudy.com/tvu.html
The technical diaries (on PDF format) can be found here:
http://www.nazaudy.com/UWL/Year%201/CCNASemester%201-Technical-Diary.pdf
http://www.nazaudy.com/UWL/Year%201/CCNA-Semester2-Technical-Diary.pdf
I passed the ICND1 on 8th April 2017 with a 86% :)
- Useful Cisco IOS CLI commands for IDND1
- Cisco, common theory
- ACLs
- Troubleshooting tips and IPv6
- VLANs
- Security
- Subnetting
- NAT
- Dynamic NAT
- Troubleshooting NAT
- Routing
- IP Classless
- Other handy commands
Useful Cisco IOS CLI commands for ICND1
These are some of the most common/useful Cisco IOS (Interconnecting Operating System) CLI (Command Line Interface) in use:
- >enable ;to switch from User Executive Mode (>) to Privilege Exec Mode (#) the hash key is used (also called pound symbol)
- #config t ;to enter Global Configuration Mode, where changes are made globally to the router/switch
- (config)#hostname ;to change the name of the router/switch (config)#no hostname ;removes the name of the switch
- (config)#banner motd %This is my banner%; to configure a banner/message of the day to show when users logon
- (config)#no banner motd ;deletes the banner
- (config)#enable password myPasswd ;activate the password to access the device so that it prompts you to logon when accessing Privileage Exec Mode (#), but really, forget about this command as it is not secure anymore
- (config)#no enable password ;removes the password from the list when you run 'show running-config'
- (config)#service password-encryption ;scribble the password so that it does not display when show running-config. This is a further layer of security particularly useful for passwords that cross the network or are stored on a TFTP server.
- (config)#enable secret cisco; this is the right command to set a password (it uses MD5 encryption);t creates the password 'cisco' to access the Privilege Exec Mode, and it really encrypts the password. When you issue this command it overrides the 'enable password'
- #show running (sh run); displays the current running configuration #show running-config (sh run); displays the current configurations
- (config)#do sh run ;use the "do" command to display the running config in the global configuration mode
- #show running-config | include hostname; display the running-config of another host
- #show running-config | include interface ;nice way to filter the display
- #show running-config | section interface ;shows all the interface
- #show running-config | section FastEthernet 0/4; display the running-config of the specified port
- #copy running-config tftp; copy the running-config to a TFTP server for backup
- #show running-config | begin line ;shows you the configuration for the console and vty (telnet-ssh) ports
- #show run ¦ begin line ;as above, very useful command!
- #show running-config vlan 1 ;shows the running configuration for vlan 1
- #show vlan ;shows the configured vlans and port association
- #show int fa 0/4; display the running config of the specified port
- #show ip interface brief (sh ip int br); display a summary of the ports with its IP address configured if any
- #show history; display the history commands used
- #show version; show the version of the running IOS on the router/switch
- #show mac address-table ;show the table of mac address the switch/router knows about it
- #terminal history size 256; specify the number of commands that are remembered, run this command on the (config-console#) and the router will remember it next time it boots.
- #terminal lengh 100; by default the size of the terminal before hitting --more-- is 24, this commands allow you to increase it
- (config)#no ip domain-lookup ;prevent from trying to resolve names when typing on the console
- #show flash ;show the information for the where the flash is
- #squeeze flash: ;compresses the flash where the ISO resides
- #reload in 5 ;reboots the devices in five minutes, no matter what doggy commands you type, cool!
- #reload cancel ;cancels the reload command
#show interfaces status ;this is a nice command, but does not work on ISO 12
#show log ;displays the log of syslog
#clear counter interface fa 0/1
- (config)#interface fastEthernet 0/0.10 ;creates a sub interface, on this example for vlan 10
- (config-subif)#encapsulation dot1Q 10 ;set the subinterface as a trunk, and instruct it to respond to vlan 10
- (config-subif)#ip address 10.0.10.1 255.255.255.0 ;sets the IP of the subinterface that will be use as gateway for vlan 10
#copy running-config startup-config; save the settings from the RAM to the NVRAM, where the IOS is stored #write memory ;does the same thing as above, but this command is slowly being faced out
- #wr mem ;same thing as above
- #copy run start ; same as above
- #write erase ;wipes out the configuration
- #reload ;after the wipe, do a reload which is basically a restart
- #delete flash:vlan.dat ;deletes the vlan config on a switch, recommended to do for a new configuration
When you copy configuration from a TFTP server to a router, choose the destination to be the startup-config (nvram) and not the running-config (ram); remember that when you copy to ram you are actually merging the charges to there
- (config-if)#line vty 0 4
- (config-line)#no login ;remove the password from the ssh/telnet ports, not advisable!
- (config-if)#line console 0
- (config-line)#password cisco
- (config-line)#login ;configure the password "cisco" for the console port (to access User Access Mode (<)); after you issue this command, use "password 7 cisco" to encrypt it
- (config-line)#exec-timeout 0 0 ;disable the timeout from the console (for lab environment only!). To enable a timeout of 5 minutes you could type exec-timeout 5 0
- (config-line)#no exec-timeout ;a different variation of the same command as above, it disables timeout completely
- (config-line)#logging synchronous ;ensure that what you type is moved to a new line when status messages appearlogg
- (config)#ip default-gateway 192.168.0.1 ;sets the default IP address
- (config)# interface vlan 1 ;enter to configure VLAN 1, the default vlan
- (config-if)#ip address 192.168.0.10 255.255.255.0 ;configure this ip on the vlan 1
- (config-if)#no shutdown ;enables the interface and set its status to up
- (config)#interface fa 0/1; allows you to access the given port for configuration
- (config)#interface range fa 0/1 - 10 ;the 'range' command allows you to select more than 1 port for configuration
- (config-if-range)#shutdown ;shutdown all these selected 10 ports
- (config-if)#duplex full ;set the speed to full, use this on port connected to other network devices, switches and routers
- (config-if)#duplex auto ;set the speed to auto, use this on ports connected to end devices, computers and printers
- (config-if)#speed 100 ;hard code the port to be at 100 MBps
- (config)#ip domain-name nazaudy.internal ;configures a domain name on the switch for encryption
- (config)#crypto key generate rsa ;generate a key certificate for encryption, you'll be prompted next for the size of the key to be in the range of 360 to 2045, the default is [512], but recommended is to use 2048. Note that the generated key will be non-exportable
- (config)#ip ssh version 2 ;enables the generated keys, version 2 has more features but only works for key that are at least 768 bits; (version 1 is old and obsolete)
- (config)#line vty 0 15 ;selects all remote ports, where we are going to enable now the generated encrypted keys
- (config-line)#transport input ssh ;this command effectively disables telnet, because you are only allowing ssh through the vty lines
- (config-line)#transport input all ;on other hand this command enables both ssh and telnet, not what we want
- (config-line)#login local ;this command force the use of username and password from the local database, disabling the master password setup when configuring the switch. After you type the "login local", go back to config mode and type the needed username and password that you want:
- (config)#username myUsername secret myPassword ;creates a username that is needed in order to use the generated key
- #show users ;it shows you the user logging to the system
- #clear line vty 3 ;log out the user from whichever line he/she is connected, on this example vty line 3
A TACAS server is a server where the usernames and passwords for the switches are stored
Port Security; allows you to restrict the connections to a Network in two ways:
- By limiting the number of MAC addresses per port [protect]
- By specifying what MAC address are authorise to connect to a port [restrict]
Trunk ports are not valid for port security; for port security to work the mode has to be set as "access", meaning that it is the expectation that only one device will be attached to the port set as access. Ports by default are set to "dynamic", which is dangeours as they can flip from 'trunk' to 'access' without us knowing it
- (config-if)#switchport mode access ;configures the port to be on access mode, thus allowing port security
- (config-if)#switchport port-security maximum 1 ;set to 1 the number of devices (mac addresses) that can be connected to the port, sometimes you have to set it to 2 is, for example, there is a daisy chain connection in use (IP phone + computer using the same port)
- (config-if)#switchport port-security mac addresses 00-11-22-33-44-55 ;add the mac address to the port white list
- (config-fi)#switchport port-security mac addresses sticky ;convert the already mac addresses on the table to be the only one accessible
- (config-if)#switchport port-security violation shutdown ;shuts the port down when a violation of the security occurs
- (config-if)#switchport port-security ;finally, this command turns on the feature, so don't forget to type it!
- (config-if)#show port-security ;shows the configuration of the port and the action it will take when a violation occurs
- (config-if)#show port-security address ;shows the white listed mac address/addresses
Only when you check the port interface you can realised that the port has been shutdown (err-disabled) due to a violation of the port-security requirements. To enable the port again, use the "shutdown" command to shut the port down (thus removing the err-disabled status) and then "no shutdown" to put the port on operational mode again.
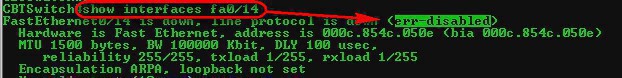
You can use the do command from any configuration mode to call commands (like the show) that do not belong to the particular configuration mode you're in
Get rid of the old-legacy unencrypted enable password by typing "no enable password" at the Global config mode, this will default the switch to use "enable secret" which is way more secure (the enable password is there only for backward compatibility)
Shortcuts
- Ctrl-R; redisplay a line
- Ctrl-Z; exit the configuration mode
- Ctrl-Shift-6; interrupt a process like the ping command or traceroute. Issue the command
- Ctrl-C; abort the current command and exit the configuration mode
Cisco, common theory for Exam 100-105 IDND1
It is recommended to set the port speed (auto, full or half) on ports between infrastructure devices, between switches and routers; on all other ports towards end devices (computers, printers, etc) the auto mode is recommended
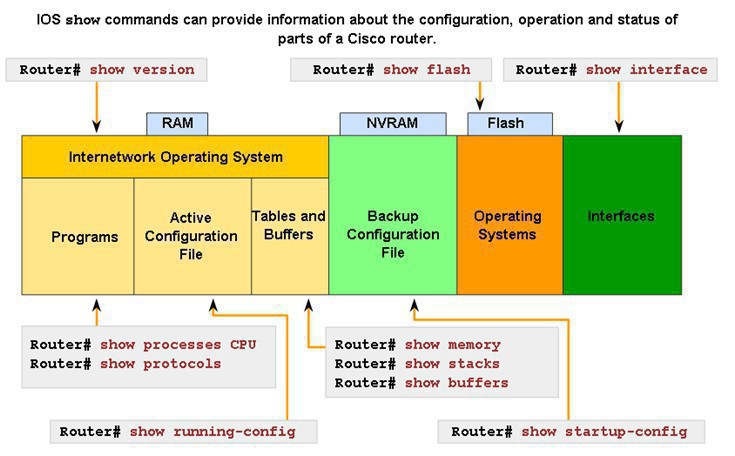
If the Cisco switch/router is booting and does not find a NVRAM configuration file (or the file is corrupted), it will enter on basic configuration mode, prompting you to enter details for a basic configuration. Notice from the diagram above that the ISO is stored on RAM, from where is loaded into flash upon starting, then it reads its configuration from the NVRAM
To troubleshoot a slow network, check the following:
- Full/Half duplex connections? particularly for printers and phones which normally are at 100 MBps; general devices are to be set to auto-detect (as long as they run +1GB nic cards!), while connections router-to-router or switch-to-switch are to be set to the specific speed
- Collision packets? There should be no collisions whatsoever on a given network; collisions occurs when colliding packets sent to mismatch half/full duplex happens, and both devices send at the same time hence dropping packets. This will cause the network to slow down
- Crossover cables? Computer-connection-to-switches should use a straight-through cable while switch-to-switch should use a cross over cable; that was true until MDIX came out and detected the cable automatically, but... do you have an old switch without MDIX (which by the way relies on auto-negotiation)? are you using the right cable?
- Check counters, run show int fa 0/1 or whichever interface is affected and make sure the collisions are zero, there SHOULD NEVER be collisions. "Late Collisions" are always an indicative of duplex mismatch, while "Collisions" are on the hub world, which occurs on the first 32-bit of a transmission
- When using tracert, it is best practise to use it with the switch -t (tracert -t), otherwise the command will take forever trying to resolve names
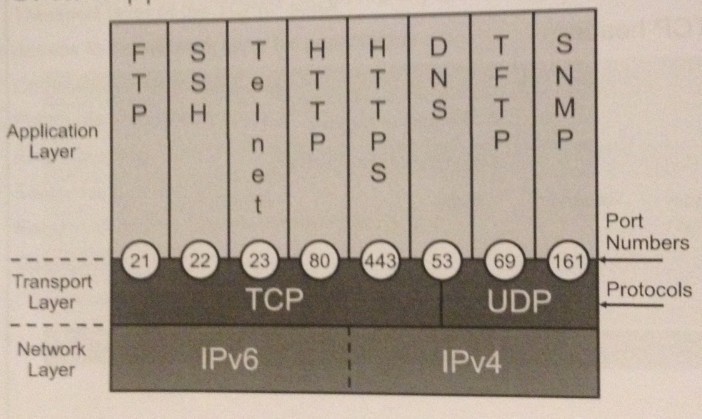
TCP (connection-oriented, reliable) and UDP (connectionless, best-effort) are protocols that operate both at the Transport Layer
ACLs
After the ACL is configured, it should be linked to an interface using the ip access-group command. Only one ACL is allowed per protocol, per direction and per interface
Extended ACLs are numbered from 100 to 199 and from 2000 to 2699, providing a total of 800 extended ACLs that you can use
Named ACLs allow you to add, modify or delete individual entries in the specified ACL; you can use sequence numbers (in slots of 10) to insert statements anywhere in the named ACL
ACL Guidelines:
- The most specific statement should be at the top of the ACL, while the most general statement should be at the bottom
- The last ACL test is always an implicit deny all, so every list needs to have at least one permit statement
- When placing ACL in a network, do as follows:
- Place extended ACLs close to the source
- Place standard ACLs close to the destination
- When placing ACL in a network, do as follows:
When you want to block Telnet traffic into and out of the router itself, use the access-class command to appy ACLs to the vty lines
MAC Addresses are composed of 48-bits, the first 24-bits are called OUI (Organisation Unique Identifier) and identifies the manufacturer of the network card, while the remaining 24-bits are called end-station address and uniquely identifies the ethernet address on the nic
Network switches learn and maintain a copy of the MAC address on the network so that they can switch/forward packets effectively
To discover the mac address of a computer and on which port is located in a switch, do as follows:
- Ping the IP address, so that its mac address is added to the mac address table of your computer
- If ping is successful, run arp -a command on your computer, to see the list of mac addresses
- Then, on the switch, run show mac address-table ¦ i 0101 where the 0101 is the termination of the mac address; the result will tell you on which port that mac address is located.
IPv6; it does not support broadcast like IPv4 does, instead it uses "anycast": when a packet is sent to an anycast address, it routed to the nearest interface that has this address, based on the measure of distance of the particular routing protocol.
Type of Unicast addresses:
- Global; starts with 2003::/3 and are assigned by IANA
- Privave; starts with FE80::/10, and you find in this category the loopback (::1) and unspecified (::)
Trunks carry all VLANs all the time; "trunk" is a terminology term used by Cisco, every body elses uses the term "tag", and what is that is to pass multi-vlan information between switches. 802.1Q (Standard) and ISL (Cisco propierary) are the protocols used to tag packets as they go through a trunk port. 802.1Q inserts a 4-byte tag fields in between the "Source Address" and "Type of Length" fields of the frame, then it recomputes the FCS on the modified (now tagged) frame
Configurations for VLANs 1 to 1005 are written to the vlan database file (vlan.dat)
VLAN tag are always removed when the packet arrived to the end device (computer, etc)
If a trunk receives a packet that does not have any tag on it, it automatically assign the packet to the native vlan (vlan 1)
#show cdp neighbours ;shows the Cisco devices that the CDP protocol has discovered
IP phones do understand the protocol 802.1Q, and automatically tag their outgoing packets with whichever VLANs they have been configured. Packets from end devices like computer/printers, are tagged once they reach their switch (this means that the end devices are by default on VLAN1)
Always ensure that the native VLAN matches in between switches; the recommended option is to leave it as default (set it a VLAN 1)
VTP (Vlan Trunking Protocol) is NOT actually a trunking protocol, the only trunking protocols are ISL (already obsolete) and 802.1Q; the VTP Trunking Protocol should be understood as a "replication" VLAN protocol. When using VTP, all switches participating in VTP start with "revision 1", and once a change (the addition of a VLAN for example) is added to the switch, that configuration is replicated to all VTP switches that are part of the VTP domain
Be very careful when using VTP: if you add a switch (third-party maybe) that has for some kind of revision higher that other switches it will override their VLANs with the one of the last/higher revision. In these situations, the ports will become "amber", as they are configured with a VLAN that has been deleted by the latest revision, and not finding the VLANs that they have been assigned, they simply will shut themselves down.
VTP can only have these modes on a give switch:
- Server Mode (default); out of the box, a switch is set on VTP server mode, meaning it you can save VLAN configuration to it, as well as send and receives VTP updates
- Client Mode; on this mode, the switch does not save any VLAN configuration, it is able to send/receives updates but to make changes to the VLAN configuration: you have to do it on the Server Mode Switch
- Transparent Mode ; the recommended by Cisco, essentially it means that the switch is not using VTP, it does receives and forwards VTP updates, but does not send its VLAN configuration neither saves any VTP VLAN configuration
VTP Pruning; it only works when using VTP switches, and what it does is to keep unnecessary broadcast traffic from crossing trunk links
Really, you should never have the outside world, the DMZ and the inside world connected on the same switch/router (unless you have set your VLAN in the very right way on the given switch where all these lans are configured/connected)
A good security practice is to separate the management network from the data (so that nobody can use telnet against a switch), as well as to change the native vlan to something of your choice by issue this command on each end of the trunk ports: switchport trunk native vlan 99
To create VLANs follow:
- (config-)#vlan 10 ;that will create vlan number 10
- (config-vlan)#name FINANCE ;that will rename the current vlan just created to finance, good practice is to set the name in capital letters to later quickly identify it
- config)#int fa 0/24 ;after creating the VLAN, visit the port where the PC is connected
- (config-if)#switchport mode access ;and set that port to access mode
- (config)#int fa 0/1 ;then, visit the port that connects the switch to the router
- (config-if)#switchport mode trunk ;and set that port to trunk, so that it can pass through vlan traffic
- (config)#no vlan 10 ;removes vlan number
- #show vtp status ;shows the configuration of VTP, whether it is client, server or transparent
- (config)#vtp mode transparent ;do this to turn off VTP, the only way to disable it is to make it transparent
- (config)#vtp domain NULL ;set the vtp domain to nothing
- (config-if)#switchport nonegotiate ;turn off VTP advertisement on the port, make the traffic quicker
- (config-if)#switchport mode trunk native vlan 5 ;set the native vlan to 5, really not recommended, all should be to 1
- (config-if)#spanning-tree portfast ;disables spanning tree protocol on the selected ports
- #show interfaces fa0/1 switchport ;displays the VLAN the port belong to
To extreme VLAN security, make sure you hard code all your trunk ports, meaning to disable the "dynamic desirable" by entering the following global command:
- (config)#interface range fastEthernet 0/1 - 24
- (config-if-range)#switchport mode access
Then, individually select the ports that need to be on switchport mode trunk as you go along
To create a trunk port do the following:
- (config-if)#switchport trunk encapsulation dot1q
- (config-if)#switchport mode trunk
To create subinterfaces for a specific port in a router, do as follows:
- (config-if)#int fastEthernet 0/0.10 ;creates a subinterface for the router
- (config-subif)#encapsulation dot1q 10 ;that tell the interface to grab any packets with the vlan tag 10; this command needs to be run before setting an IP to the subinterface
- (config-subif)#ip address 10.10.10.1 255.255.255.0 ;that would be the gateway IP for vlan 10
- #show interfaces trunk ;shows you all the vlans that are passing through the trunk ports, if you do not wish to allow all the listed vlans to pass through this port, use this command:
- (config-if)#switchport trunk allowed vlan 10, 20 ;that will allow only the typed vlan through the selected trunk port, if you want to add one more vlan to the above, enter this command:
- (config-if)#switchport trunk allowed vlan add 30
If you know the number of networks needed, then do as follows:
Determine the number of network in binary, so that you find out how many bits are needed to reach that number, for example:
- To reach 9 networks, 4 bits are needed = 0000 1001 (last 4 bits are needed to make up number 9)
- To reach 14 networks, 4 bits are needed =0000 1110 (last 4 bits are needed to make up number 14)
- To reach 19 networks, 5 bits are needed = 0001 0011 (last 5 bits are needed to make up number 19)
Once you know the number of bits that are needed to make up the given network, subnet those bits from the given subnet mask, for example:
For a network 255.255.255.0, if we want to have 9 networks, 4 bits need to be borrowed:
- 11111111.11111111.11111111.00000000 = 255.255.255.0
- 11111111.11111111.11111111.1111.0000 = 255.255.255.248 [4 bits has been borrowed to make the new subnetted mask]
Finally, the increment is the lowest network bit in decimal, on whichever octet it is placed (do not consider the other octets, only the value of that last one borrowed bit "1")
NAT translates the private IP address (inside local) to the public external IP address (inside global). To configure NAT on a router follow these steps:
- (config)#interface GigabitEthernet 0/1
- (config-if)#ip address 210.11.12.13 255.255.255.240 ;give a public IP to the Gig 0/1 interface to the inside global
- (config-if)#ip nat outside ;set that interface to be facing the outside world
- (config-if)#exit ;back to global configuration
- (config)#interface GigabitEthernet 0/0
- (config-if)#ip address 10.10.10.13 255.255.255.240 ;
- (config-if)#ip nat inside ;set a private IP on the interface to be protecting the inside network
- (config-if)#exit ;exit back to global configuration
- (config)#ip nat inside source static 10.10.10.13 210.11.12.13 ;establish the static translation between an inside local and inside global
Dynamic NAT
The ip nat pool defines a pool of IP addresses to be permitted in the access list (page 2155), where the translation happens by NAT picking up one of those public IP addresses from the pool
Troubleshooting NAT
Use these commands to troubleshoot problems with NAT
- show ip nat translations
- show ip nat statistics
- show access-list
- show ip route
Rule of "specificity", the route that is most specific always wins
- #show ip route ;displays the table of configured routes
- (config)#ip route 192.168.3.0 255.255.255.0 192.168.1.1 ;instruct the router to use the next hop IP (192.168.1.1, which is the IP of another connected router) in order to reach the network 192.168.3.0
- (config)#ip route 172.16.3.0 255.255.255.0 serial 0/0/0 ;instruct the router to use its interface serial 0/0/0 in order to reach the network 172.16.3.0
- #ping 192.168.0.1 source 192.168.1.1 ;this command instruct the router to ping to the address 192.168.0.1 but using the interface connected to 192.168.1.1, nice command to know for troubleshooting
- (config)#router ospf 23 ;configures the router to use ospf, with the process id of 23, this process id is entirely your choice
- #show ip arp ;displays the arp tables of the switch/router, matching IP address with MAC addresses
The 0.0.0.0 network address and mask 0.0.0.0 is called the quad-zero route
Interior Gateway Protocols (IGPs) are RIPv2, EIGRP and OSPF; they route within a single Autonomous System (AS), a collection of networks. IGPs can further be divided as follows:
- Distance vector (RIP); use a metric such a hope count, and they send the whole routing table on the updated (RIPv1 used to)
- Advance distance vector (EIGRP); uses a Hello protocol to discover neighbors to whom it establish a relationships and periodically sends updates, which are partial and only when a change occurs
- Link-State (OSPF, IS-IS); uses the SPF algorithm to create an abstraction of the exact topology map of the entire internetwork. All link-state routers use its own internal map of the network and calculate the shortest paths to reach the destination network in relation to where they are on the map. Link State Advertisement (LSA) are sent periodically, every 30' by default and to the multicast address 224.0.05
Exterior Gateway Protocols (EGPs) are design for use between Autonomous Systems that are under the control of different administrations; BGP -border gateway protocol - is an example.
Administrative Distance of Routing Protocols:
- 0 - Directly connected interface
- 1- Static route that has been configured
- 20 - BGP (Border Gateway Protocol)
- 90 - EIGRP
- 100 - IGRP
- 110 - OSPF (Open Shortest Path First)
- 115 - IS-IS (Intermediate-System to Intermediate-System)
- 120 - RIP (Routing Information Protocol), uses hops as metric
OSFP routing; uses hello packets for communication, but it only sends the packets once it has a partnetship with a router (partnership is only achieved when timer, subnet maks, security to access the area, etc, are all checked) Routers running OSFP have a "timer" to, let's say 30 seconds; timers between routers must match (otherwise they won't form a relationship) an if a router does not hear from another router within the timer span, it deletes its routes from its table. Areas of a OSFP domain represent an area of summarization. OSPF uses cost as a metric
The route-map ;this command is used to enable policy routing or conditions for router redistribution from one protocol to another
Routers support 3 types of packet-forwarding mechanisms: Process switching (the oldest, where every packet is treated in full), Fast switching (where a cache is created to improve speed) and Cisco Express Forwarding (where the changed in the cache are change-trigerred -changes on the network- and not packet-triggered, being therefore this method quicker and more proactive)
Routes that are directly connected to an interface (C) are removed from the routing table when the interface has failed or is administratively down. Note that directly connected routes overrride the Static routes that you may have configure on a router.
The router changes the source and destination MAC addresses, while source and destination IP addresses remain the same. Remember that a switch does not change the frame in any way, it simply forward it to the appropriate port according to its MAC address table.
Frames sent to the default gateway have the local host source MAC address and the default gateway destination MAC address
To enable routing on a router do as follows:
- #conf t ;enter global configuration mode
- (config)#router rip ;enter router configuration mode for the rip protocol
- (config-router)#network 192.168.15.0 ;
The RIP network command tells RIP what network to advertise, for example the command (config)#network 10.0.0.0 will advertise all network starting with 10.x/ 24. IN ADDITION, the use of that command will also implies that these networks that have just been advertised, will be advertised by other routers
IP classless ;instruct the router to use its default IP ROUTE to forward packets for unknown networks
(config-router)#no auto-summary ;
Other handy commands
#show spanning-tree vlan x ;this command is used on a Catalyst 6500 series switch to view the spanning-tree protocol information on that specific vlan
#traceroute ;follow the path of a packet as it is being transmitted across the network, not that windows users tracert command while ciso IOS and Linux OS only uses the traceroute syntax
#no cdp run; disables the CDP protocol globally on a router. Remember the CDP is a layer 2 protocol therefore only detects directly connected cisco devices. The command #no cdp enable only disables the CDP on that specific interface
- (config)#access-list 1 permit 172.16.0.0 0.0255.255 ;this statement matches any IP coming from 172.16.x.x
- #show access-lists ;displays the configured access list on the router
- (config)#no access-list 1 ;deleted the access list number 1
c:\arp -a ; displays the MAC address table that your computer knows about
T568A; starts with the green-white and finished with the brown, flipping the orange
T568B; starts with the orange white, finishing alwasy with the brown but flipping the green
Straight-Through; to connect unlike devices (I'm straight, so I like unlike devices, like women ;)). It has either T568A matching at each end or T568B matching at each end
Cross-over cable; it has T568A at one end and T568B in the other
Rollover cable; where pin 1 correspond to pin 12 on the other end, pin 2 to pin 11, etc
netstat; shows all connections to your computer
SecureCRT is an alternative to Telnet (though I prefer SuperPutty). Also explore Putty Connection Manager
Jeremy's rule: when ordering infrastructure stuff remember: one is none, two is one (redundancy is paramount). Our job is to be invisible.
Collapse Core Model, is the most typical hierarchy model for Cisco switches
Please Do Not Through Sausage Pizza Away. All People Seem To Need Data Protection
SmartNet is a packet support plan that you should buy for your Cisco device, cost lots though
MiniCom is putty for iMacs
Get tutorial and ISO download for GNS3 here: http://protechgurus.com/download-gns3-ios-images/
CDP is enabled by default in Cisco IOS 15.0 and later
#show mac address-table ;shows the mac address table on a switch
#show arp ;does the same thing as above
#debug matm all ;shows all activity dealing with mac adddress, careful wtih the debug comand!
Remember a switch is a layer 2 device, therefore it does NOT need IP address, only for management purpose we put an IP on it
If the switch port is in full-duplex mode and the attached device is in half-duplex mode, check for FCS erros on the swtich full-duplex port
<Control + Shift + 6 > then press "x" at the console to terminate the telnet connection to a device and come back to your screen
ASIC-Based routing is basically layer 3 switching
London, 8 April 2017
If you enjoyed the reading of this article about Technical notes for Cisco Certification Exam 100-105 ICND1, surely you'd love this other one too:
References
- http://speedof.me/
- http://cfn.cloudapps.cisco.com/ITDIT/CFN/jsp/index.jsp (by just typing cisco.go.fn)
- http://freeciscolab.com/free-downloads/
- https://www.mindhub.com/Cisco-Certification-mindhub-s/25.htm
- https://pentestlab.blog/2012/03/05/common-tcpip-ports/
- http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4500/12-2/20ewa/configuration/guide/conf/port_sec.html
- https://cfn.cloudapps.cisco.com/ITDIT/CFN/jsp/compareImages.jsp