Lab Setup for Microsoft Exam Azure AZ-900
In this article I explore the contents theory for the Microsoft Exam Azure AZ-900, so you can revise and actually do some testing before taking the AZ-900 exam. I didn't have any Azure certification, and it was long overdue for me to jump into the pool of the cloud (yes, take the plunge!). Sooner or later, the maintenance of an on-prem infrastructure will disappear, think about it: a brand new business most likely will have its infrastructure on the cloud, rather than facing the initial investment of an in-house without knowing if the company is going to do well or not
So, let's go and focus, study hard and get Microsoft Azure Fundamentals certified. The topics for the Exam AZ-900: Microsoft Azure Fundamentals can be found here: https://docs.microsoft.com/en-us/learn/certifications/exams/az-900 , these topics were last updated by Microsoft 23rd January 2024, and that update is the one used in this article
The Cloud could be described as simply using somebody else's CPU and memory, basically somebody else computer. Just so we understand the concept, let me share this video with you. It is an ancient video relating to a VMware product, but to me it clearly demonstrates what cloud computing (name it Azure, VMware or Google Cloud) can do for you, how flexible "borrowing" resources from the Cloud could be for your business:
These are the contents of this article:
- Azure - starting up
- Cloud Concepts
- Azure Architecture
- Azure Infrastructure
- Compute, Networking, Storage and Database
- Authentication and Authorisation
- Azure Solutions
- Security
- Monitoring and Management
- Pricing
- Support
To convince your business to adopt Azure or any other cloud platform, re-direct them to the Cloud Adoption Framework for Azure: https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ where you'll find strategies that will be useful for your business to succeed in the cloud
Start by registering your email account with Microsoft. If so, then use it to sign up at Azure Portal here: https://azure.microsoft.com/en-gb/free/ You'll get lots of things with this new account, and it is absolutely perfect to explore Azure and do some testing without messing up with your production environment
During the setup process, you will need to verify your account by entering your mobile number (notice VoIP phone numbers are not allowed for some silly reason) and a valid credit card number. There is no way to avoid this, so just do it! Unfortunately, you only got one month to test Azure, after that you'll get the "not eligible" message if you try to register again with another account
Even if you sign it with a different credit card number, Microsoft Azure won't allow you to "cheat" and duplicate the account, so basically you only have one flipping month to use the free service. Be wise and use it just to prepare for this exam! You can create multiple subscriptions in a single Azure Active Directory tenant
The main topics for the AZ-900 exams are:
- Cloud Concepts
- Azure Architecture
- Azure Infrastructure: Compute, Networking, Storage and Database
- Authentication and Authorisation
- Azure Solutions
- Security: Privacy, Compliance and Trust
- Monitoring and Management
- Pricing
- Support
The tools you need to be familiar with to pass this exam are:
- Azure Portal
- Azure Cloud Shell (Azure CLI and Azure PowerShell)
- Azure Mobile Apps (download the app for IOS or Android, so you can access Azure from your smartphone)
- ARM Templates (automate and simplify Azure resources)
The 7 main concepts that are use when working with the Cloud are:
- High Availability; means that the systems are always available, even automatically; this is achieve by using different datacenters in Azure
- Reliability; describes how Azure can tolerate failures or even disasters
- Scalability; refers to scaling out or scaling up while automatically providing resources as needed
- Predictability; is knowing that your application will always perform as expected and knowing what it will cost
- Security; is having full control of your cloud security posture
- Governance; is standardising cloud deployments to meet requirements and company standards
- Manageability; is management of cloud resources and how we interact with them
The National Institute for Standards in Technology (NIST) defines Cloud Computing as having the characteristics of pay-per-use, resource pooling, rapid elasticity of resources and on-demand self-service. There are basically 3 types of Delivery Models of the Cloud, and your company may need one, two or all three models implemented, it depends:
- IaaS: Infrastructure as a Service (datacenters); you move virtualisation, servers, storage and networking to the Cloud. This is the most flexible way of using the Cloud but you still need someone to look after the firewalls, networking and Operating Systems. Larger providers of this are Amazon Web Services, Microsoft Azure and Google Cloud Platform
- PaaS: Platform as a Service (web browsers); deploy applications on the cloud, focused on developers where you only have to worry for your apps. PaaS lies on IaaS to work, and with PaaS you don't have to worry about the OS, windows updates, IIS configuration, networking, storage, etc. A large provider of this is Google App Engine, AWS's Elastic Beanstalk or some part of Azure too. For example, with PaaS you can use Azure SQL instead of a VM with your SQL on it. PaaS includes Middleware, which is software that lies in between your apps and the OS. You can get lots of middleware apps from the Azure Marketplace, all of them built to save you time. You can find the Azure Marketplace in this link: https://azuremarketplace.microsoft.com/en-us/marketplace/ Azure Marketplace offer less maintenance than creating your own service or application from scratch
- SaaS; Software as a Service (cloud services), the most popular way of using the Cloud. With this method the client just uses a cloud-based app something like email, Office 365 or storage (dropbox, oneDrive, box.com, etc). A large provider of this is Salesforce, providing cheaper ways to consume enterprises applications such as CRM and ERP, also consider Google Apps for Work (automation on demand) and Microsoft 365 (office over the open Internet). Other software solutions like Finance and expense tracking, email or ticketing systems use SaaS

Depending on the Model used above (IaaS, PaaS or SaaS), the Shared Responsibility Model will also change, thou at all time you are responsibly for your data and accounts

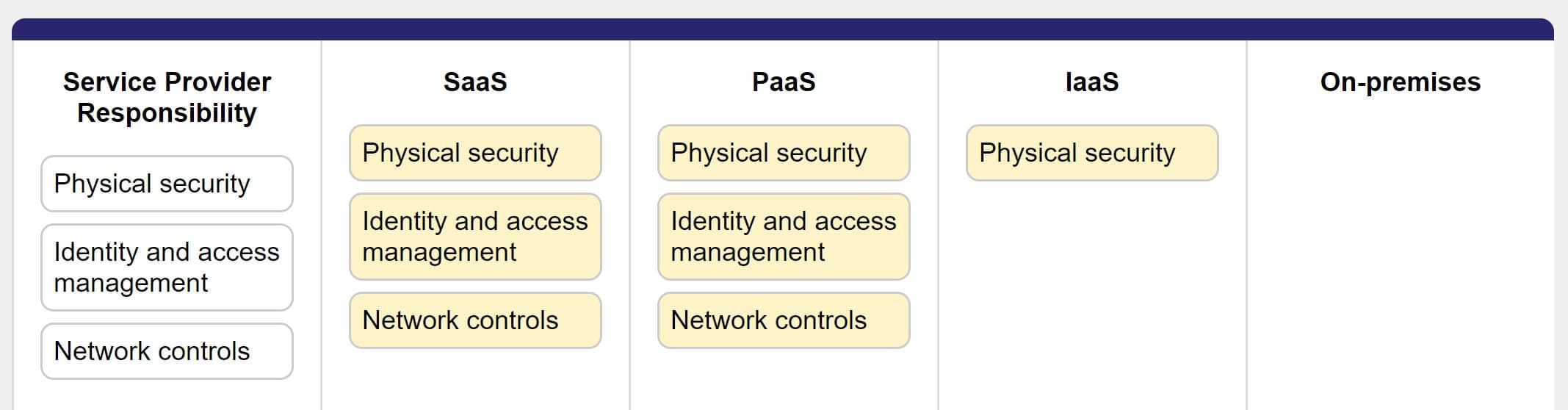
In addition to these 3 main cloud-model, there are also these specific ones like:
- DSaaS; Data Science as a Service, outsources the delivery of data that is gathered via progressive analytics applications
- NaaS; Network as a Service, outsources services for network transport connectivity such as routers and subnets
Economy of Scale: you can buy one apple for £1, but if you buy 100 apples all at once, each apple might cost you just 10 pence each. Rocket Science ah? :) Economy of Scale can be apply to these two things;
- CapEX (Capital Expenditure); you spent money upfront as a one time purchase for hardware, e.g. you buy a laptop. Problem is that the value of the item will go down with time. Examples of CapEx is deploying an Azure reserved VM instance, BUT a normal Azure VM is an example of OpEx. More example of CapEx are server cost, storage cost, technical personnel cost, backup and archive costs, disaster recovery costs
- OpEx (Operational Expenditure); recurring cost of a service, you go and subscribe to a payment plan with Apple, and every month you pay and always have the latest phone of the market. This is a more agile approach, and can be described as the ongoing cost needed to run your business. Examples of OpEx are employee salaries, rent, utilities, property taxes
Cloud Architecture Model (Deployment Models of the Cloud,) you can implement the Cloud in your company in basically 3 ways, but of course you have to UNDERSTAND the workloads first before suggesting anything
Public; (elastic scaling) everything is at the provider's end, you put all your VMs on Azure and that's it. That gives you Scalability/Agility, pay-as-you-go, some of your VMs could be running very sensitive-data, so you might prefer to have them on-prem. This model provides the best security
- Agility is the capacity to react quickly, providing on-demand services in minutes without manual intervention
- Elasticity, is a feature that increases or decreases resources automatically
- Scalability also increases or decreases resources, but this is done manually
Private; (more secure) it behaves like a public cloud but the company owns all the infrastructure, is like having VMware vSphere where you own all the kit and your provide cloud services to your company. Government entities will do that, for example. This method is not very flexible, and also you need to contract the IT personnel to support this
Hybrid; (seamless, of the two above) this is mixed of the two, with some services running on a private datacenter (running Hyper-V or VMware vSphere) and others in the public cloud (Azure or AWS). Note that connecting your private cloud to your public cloud could be a complex task and requires skilled IT personnel (like us :)) This model can be the best of all models, but it incurs in lots of complexity to setup
- AD Connect Tool; integrates your local AD to Azure, sync users groups and computers and provides SSO and ADFS, thus making you a hybrid mutant, and allowing your users to access both your on-prem and cloud resources
Azure Regions: be mindful, you don't want to deploy your IIS server in Europe if your main customers are based in South-East-Asia (SEA). For logistical purposes, Azure geographical areas may contain one or more regions. To minimize latency, you want a datacenter that is on the closest region from where you are. Price varies from Region to Region, as well as features. Azure Region is a set of datacenters that are close enough to each other, so that it doesn't matter which datacenter your data is in, becuase you'll get the same latency
Region Pairs; reduce or eliminate downtime by power or network outages. In Azure, each Region is pair with another Region (except Brazil South), these two regions that are at least 300 miles from one to another (within the same geography area) where one region kind of functions as the backup of the other. When doing planned updates, only one Region in the pair is updated at any one time
Availability Zones; they are physically separate locations within an Azure Region, in other words isolated datacenters; if you create 2 x VMs (master & replica) and put them on the same region, the replica will go to an availability zone, physically away from the production area. Availability Zone is within a Region, and each zone has its own separated power, cooling and networking. Every region has 3 separated availability zones to ensure resilience
Availability Sets; they are logical groups of 2 or more VMs that you want to ensure remain up and running during plan (or unplanned) periods of downtime, this is achieved by basically putting the VMs on different rack servers if they fall on the same datacenter. Note that you can only mark a VM with High Availability at its creation point, once it is created you'd need to delete it if you want it to be part of an availability set. If you forget to put your infrastructure on an availability set, it is possible that all of it could be restarted at once, when Azure does update of the datacenter where all your VMs are, therefore it is advisable to configure the "Availability Set" at the time of creating the VMs, to ensure that you have a high SLA. When you create an availability set, each VM in the set is assigned a Fault Domain (things that can fail together, like common switches an power source) and an Update Domain (racks that can be updated and rebooted together)
- Using the Azure Resource Manager (ARM) portal, you can configure up to 3 Fault domains and 20 Update domains
- Using the Azure Service Manager (ASM) portal, you can configure up to 2 Fault domains and up to 5 Update domains
SLA 95%, a single instance using a s standard HDD
SLA 99.95% (21 minutes downtime a month) involves two or more instances in the same Availability zone
SLA 99.99% (1 minute 26 seconds downtime a day), involves two or more instances across two or more Availability zones, in the same region
Composite SLA; this is when you combine 1 or more SLA that are dependable of one another for a complete solution to run effectively. For example you have a Web Front End VM that needs to run 99.95 % of the time, and a SQL database which feeds that server that needs to run at 99.99%. When you combine those SLA times you get a composite SLA of 99.4%
Azure Batch; is like scale sets but on steroids, where you can deploy hundred or thousand of computer
Resource Group; Everything in Azure is inside a Resource Group, no exceptions, but note that a Resource Group itself is not a resource, they help structure your Azure architecture. They are used to logically group your stuff, the items in a Resources group can expand different regions, but the actual resource group, its metadata, can only reside in one location. Resource Groups cannot be renamed once created and cannot be part of a Resource Group. All resources in your Resource Group should share the same lifecycle, they are all updated, deployed and deleted together
new-azresourcegroup -name NazaudyRG -location 'East US 2'
When you delete a resources group, Resource Manager uses this criteria to execute your deletion command:
- All nested child resources are deleted first
- All resources that manage other resources (indicated by the property managedBy on the managed resource) are deleted next
- The remaining resources are deleted next, without following any chronological order
- Resource Manager will continue trying the DELETE call every 15' when a resource respond with an error status 408, 428 or 5xx
Resources inside Resource Groups can be moved to another Resource Group within the same subscription or to another subscription, but during the move operation the source Resource Group and the target Resource Groups are both locked, meaning you cannot add, update or delete the contents of the Resource Group until the move is completed
Azure Resource Manager (ARM); when interacting with resources you are interacting with ARM, whether you go with the web, PowerCLI, etc, so basically ARM is the key component of Azure Portal itself, the core engine. All interaction with Azure resources go through the ARM
ARM Templates; let's say you create a resource for your website, which obviously will contain 2 x VMS (web end + database) in addition to network connections, virtual IPs, storage, etc. You can save this resource creation as an ARM Template, which will be saved on a JSON file, in case you want to deploy the same solution again in the future
Cloud Shell; visit https://shell.azure.com or click the PS icon on the top-right corner of the Azure Portal to start Powershell (if you're using Windows) or Bash (if you prefer a Linux environment). The 1st time you're trying to open Cloud Shell, it will ask you to create storage, I'm afraid there is no escape and you have to create it, check here the pricing list for this storage:
The cheapest option, obviously, is to download to your computer and install Microsoft Azure CLI: https://learn.microsoft.com/en-us/cli/azure/install-azure-cli-windows?tabs=azure-cli Once you install it, just open PowerShell and type "az" to see the commands available
You can also have Cloud Powershell on you phone too!!! (Azure mobile app), fire up some VMs while you queue up for a coffee
Azure CLI; Microsoft developed this as a transition between Powershell and the portal. You use the Cloud Shell window to run Azure CLI commands, all CLI commands start with "az" , you can install it on macOS, Linux and Windows for automation of tasks. Azure CLI is definitely the way to go when working with Azure because is stable, its commands don't change, the CLI commands are structured in a way that is logical and is Cross-Platform (you can use it in Linux), it provides Automation, routing operations with scripts, standardise database failovers, data pull to provide powerful insights and Logging; Azure CLI and PowerShell are great to perform repeatable testing, management and administration tasks, so Go Azure CLI! JSON is the default output format for Azure CLI, service principals are used to secure it (these are account not tie to a specific user), CLI configurations are saved in INI format, and unfortunately Azure Classic CLI is no longer supported or maintained
az (focus) xxx (group) xxx (subgroup) xxx (base comannd) --xxx (required arguments)
--xxx (optional arguments)
--xxx (global arguments)
az vm -h #calls for help to see what you can do with the group "vm"
az vm create -h #again, the -h will shows you the options for the "create" subgroup
az vm create --resource-group myRG --name myVM01 --image ubuntuOS --generate-ssh-keys
az vm show
az vm list
az vm deallocate --name VM01 -g myRG
For learning Azure CLI quickly, use it in "interactive" mode so that it will give you the options for you to easily choose
az interactive
az configure --defaults
#you can configure the shell to use default VMs, groups, etc to work with while commanding
Some handy Azure powershell commands:
- Get-CloudDrive
- Get-AzResourceGroup | Format-Table
- Invoke-WebRequest -Uri "https://raw.githubusercontent.com/BrentenDovey-ACG/AZ-104_Azure_Administrator/master/cleanerScript.ps1" -OutFile ~/cleanerScript.ps1 #THIS WILL DOWNLOAD A SCRIPT FROM GITHUB THAT YOU CAN USE TO CLEAN YOUR ENVIRONMENT
- code cleanerscript1.ps #TO OPEN THE SCRIPT, like on the Linux text editor "vi"
This section covers Compute, Networking, Storage and Database
Compute
Creating a VM: A virtual machine in Azure is your machine exclusively. VMs are an IaaS offering, where you are responsible for the entire virtual machine. Using the Azure portal gets the clicks >>> the API chats to the Orchestrator >>> the Orchestrator send the inputs to the Fabric Controllers >>> and they push the info to the rack servers, where your VM is then created. Azure Virtual Machines take advantage of Azure tools. Even if all your VMs are off, you still will get charge for the space, so be mindful of the VM sizes when creating it
new-azvm -name VM1 -resourcegroup NazaudyRG -location 'East US 2'-image CentOS -size "Standards_bits" -credential $credential
VM Scale-Sets (VMSS); manage a group of identical, load-balanced VMs, where you can create a rule by which if a VM CPU's hits over 70% Azure can automatically create another VM, and another VM to deal with the load. Scale Sets should be deployed on multiple or separated datacenters to ensure web applications are available if a single datacenter fails, obviously they are created with VMs of the same OS image and configuration, and basically the Scale Set increase or decrease the number of instances depending on the demand
az vmss create --help
#vmss stands for Virtual Machine Scale Set
A VM with readiness unknown status, and a blue colour, indicates that is offline. We careful as well of where you place your VM, the running costs of Datacenter regions are different: having a datacenter in south-Europe will cost more than in Iceland, for example, where you pay very little for air cooling
Azure Spot VM; allows you to take advantage of unused capacity of Azure at a lower cost, but your VM can be evicted with only 30 seconds notice. VMs can be evicted based on capacity or in the configured maximum price that you set
Infrastructure as Code (IaC); enforces consistency with code development, IaC uses automated configuration that stress consistency by having well documented code that represent desired environment states. In the context of Iac, the concept of "inmutable infrastructure" means that the code is recreated rather than modified in place, enhancing consistency and reducing configuration drift
Containers in Azure: if you put your application inside a container together with all the dependencies, it should run on any machine. Containers are an important part of modern computing, they are designed for small workloads that can perform an operation quickly. You can access containers directly from a URL, and they support Role-Based Access Control. Container in Azure can be used in 2 ways
- ACI (Azure Container Instances) is a PaaS so you don't have to worry about the underlining OS or infrastructure, this is for small deployments with one or a few containers, it takes less than 30 seconds to start a container. With ACI the billing is per-second but you only pay when the container is running
- AKS (Azure Kubernetes Services), Kubernetes sometimes is pronounce "K8s", means 'governor' or 'captain' in Greek. Kubernetes is an open-source (code is available to the public) container orchestration system (keep track of lots of parts of the system), automatic deployment, scaling and management. Kubernetes allows you to replicate containers architectures, is a way to orchestrate your containers, enabling communication through APIs from one container to another. This is what to use if you have lots of containers. Kubernetes requires a YAML file for configuration. Azure Kubernetes runs in a cluster and consist of 2 computers:
- Primary computer, running a control panel that manages the cluster, the orchestration is done here
- Kubernetes nodes, these are the computers running the actual containers
Docker is a way of creating containers (an easy way), visit https://hub.docker.com/ to download images to create containers

Azure Container Registry; this service keep track of current valid container images, managing the associated files and being a repository of images from where containers and Kubernetes are created
Serverless Computing; is the abstraction of infrastructure, hardware and operating systems, where Azure automatically takes care of scaling the performance, and you only pay for the resources that you use. The name "serverless" only indicate that the servers are invisible to the developers, so they can focus on coding only. Serverless Computing allow developers to execute code based on specific events, and can be used to deliver exact units of resources when an application needs it, for example, it can give exactly 3.78 GB of RAM when demanded by the VM. Azure has two implementations for Serverless Computing: Azure Functions and Azure Logical Apps
1. Azure Functions; can execute code in almost all modern languages. Azure Functions is serverless, runs once and then stops, is the smallest compute service on Azure and can be called or invoked via a standard web address; remember that some Azure Functions can be called "Durable Functions" so don't get confused by the fact that they run once and then stop. Azure Functions allows you to execute code based on specific events, can scale on demand and is best used when demand is variable. You only get charge for the CPU when the function runs. Azure Functions can either be stateless or stateful, and can run locally or in the cloud
- Golden Oldie; the first serverless service on Azure, they are the smallest compute system in Azure
- Azure Event Grid; is a serverless routing service for sending and receiving events between applications, it directs and orchestrates events that can spark code or logic execution
Difference between Azure Functions and Azure Containers? simple, the functions are used for serverless processing while the containers are used for hosting
Difference between Azure App Service and Azure Container Apps? hhmmmm....they both do the same thing, but Azure Functions are event driven

2. Azure Logical Apps; like Azure Functions, they also trigger logic based on events, but they are stateful and only run in the cloud. Azure Apps configure workflows and choreograph processes. This serverless solutions are for workflows to those who don't know how to code but want results, it configures workflows and choreographs processes. Azure Logic Apps starts with a trigger, which fires when a specific event happens or when data meets specific criteria, they can be used to automate workloads like send email notifications, move files from SFTP to Azure Storage, monitor tweets for a specific subject, create alerts or tasks, etc

Azure App Services; is a PaaS offering from Azure where you can deploy Web Apps, API Apps, REST APIs, Web Jobs, Mobile Apps, etc without of course worrying about the infrastructure. Swagger is a standard for designing APIs https://swagger.io/ Note that Azure Apps does NOT provide any diagnoses anomalies, neither it is a serverless platform for less code. There are fundamentally 3 types of apps offering in the App Services of Azure:
- Web Apps: use to host web site and web applications using languages such as Python, Ruby, Java, ASP.NET, Core, Node.js or PHP
- Web Apps containers; all the dependencies and code are inside the containers
- WebJobs; this feature is used to run a program or script in the same context as web app, API app or mobile app
- Mobile Apps; you can use this feature to quickly build a backend for iOS and Android apps
- API apps; is an application programming interface without any GUI, REST-based APIs; they can be created using a wide range of programming languages
Note that only apps hosted in the Dedicated Computer Premium pricing tier or higher can be restored from snapshots, and that up to 100 hybrid connections can be supported by that tier
AKS Cluster; A Pod is a group of one or more containers, where K8s can provisioning pods once the load increases
Azure Virtual Desktop; this comes with different benefits like the reuse of Windows 10 license; note that under Azure Virtual Desktop remote clients cannot run MSTSC or RADC
Networking
Azure Vnet; that is the name of a network in Azure, Vnet. A virtual network is bound to one region only, meaning that every resource associated to the Vnet must be in the same region too. To see your networks nicely, visit Virtual Networks >> your vnet >> Diagram. You can essentially peer Vnet using a local balancer or using a VPN gateway to increase availability
Virtual Network Peering; makes it possible to connect to Azure network together so that they appear as one, this traffic is not encrypted because it does not travel through the Internet but across Microsoft private network
Global Virtual Network Peering; when the traffic of two or more Vnets travels across different regions
VPN Gateway; they are instrumental in a hybrid cloud architecture, and is the way you connect your Azure VMs to your on-prem VMs, the link is encrypted and, like all VPNs, occur across a very popular public connection called the Internet. When you create a VPN gateway, Azure creates for you a gateway subnet with one or more VMs that manage the VPN Gateway, you cannot connect or manage those VMs, they are there purely to provide the service. Azure VPN Gateway has a limitation of 1.5 Gbps, plus you have to pay to encrypt the traffic. There are 3 types of VPN Gateway:
- VNet-to-VNet; connect two virtual Azure network together using VPN Gateway
- Site-to-Site; connect Azure network to another network outside of Azure (on-prem network)
- Point-to-Site (P2S); creates a secure connection between Azure network and a single device outside Azure (a computer, mobile, etc). This is the only connection that does not require a public-facing IP address. A P2S VPN Gateway are useful for home users or users in remote location to connect to Azure resources. All the other connections (ExpressRoute, Site-to-Site VPN and Vnet-to-Vnet VPN) require a public IP address on one or both ends
Azure Express Route; is like VPN Gateway but with a speed of up to 10 Gbps, for which....yes, you pay more. Azure Express Route is a private network inside Azure that does not traverse the Internet, has low latency and high bandwidth connection. It is an ideal solution to migrate resources to Azure, and it establishes a direct connection from on-prem to Microsoft Cloud Services (like Azure, O365, CRM Online, etc). Microsoft calls Express Router connections a "circuit". Express Route connections are more secure and reliable than VPN Gateway based solutions and the connectivity can be:
- point-to-point (Ethernet network)
- any-to-any (IP VPN network)
- virtual cross connections through a connectivity provider at a co-location facility
Express Route Direct, the premium service, give you speed of up to 100 Gbps, as you connect directly to Microsoft using a MSEE (Microsoft Enterprise Edge Router)
Load Balancer; distributes new inbound flow (traffic from web or local network) that arrives on the Load Balancer front's end and send it to the back-end VMs according to rules and health probes that redirect the traffic according to IP and/or port number
Application Gateway; AG is a higher level of load balancer, if you want to re-direct traffic using attributes other than IP or port numbers, use an application balancer. The traffic can be specific routed using header. Application Gateway span multiple availability zones and improve fault resiliency. Application Gateway provides load-balancing for web services, in particular URL routing, and also includes a Firewall called WAF (Web Application Firewall). Application Gateway offload CPU intensive SSL (known as SSL offload or SSL bridging) and provides Layer 7 routing capabilities, including:
- round-robin distribution of incoming traffic
- cookie-bases session affinity
- URL path-based routing
- ability to host multiple websites behind a single application gateway
Content Delivery Network (CDN), it provides a "cache" (not a full replication) that is distributed as close to your customers as possible to reduce latency; this method would be cheaper. CDN places caches of your data on other datacenter physically closer to the customer's location for speed access
Azure DNS; zone that are facing the Internet are called Public Zones, and the others that are internal are Private Zones
Storage
Using the right storage for your Azure solution is critical. In Azure the "storage account" is unique in the whole of Azure, being an object with its own web address, like for example: nazaudy.storage-type.core.windows.net. When you create an Storage Account, you have the following options to use from:
- Account Type
- General Purpose v1; legacy for blobs, files, queues and tables
- General Purpose v2; recommended for blobs, files, queues and tables
- Performance Tier
- Blob storage; legacy bloc-specific accounts
- Standard; default storage performance tier
- Premium; High-performance storage tier
- Replication
- See the section "Data Redundancy" below
- Access Tier
- See below
Azure Blob; stands for Binary Large Object, the data is stored from containers into the storage account. This is use for unstructured data, and you can store files of any type like images, videos to be streamed, logs, backups. The pricing tiers of Blob can be Hot (lower access time but high cost), Cool (same as hot but data must be kept for at least 30 days) and Archive (the cheapest but the highest access time, data here must be kept for at least 180 days). Blob is organised in 3 types:
- Block Blobs; store text and binary data up to 4.7 TB, and is made up of individually managed blocks of data; best suited for streaming, images and videos
- Append Blobs; like above but are optimised for data that is appended like data coming from VMs
- Page Blobs; store files up to 8TB, and this emulate the virtual machine disk hard drive


You create a Storage Account first, then a Container within the Storage Account, and then a Blob inside the container. The process of making archived blob data online and reusable is known as rehydration, remember that Microsoft will fine you if you delete or rehydrate an Archive Blob before 180 days, and that the data in an Archive Blob cannot be copied to another Archive Blob, meaning that once you archive = 180 days do not touch
Azure disks; you have the OS disk for the VM but also the data disk, where you can store permanent data in case you want to remove the VM
Azure Files; manage file shares from on-prem to the cloud, and are accessible via Server Message Block (SM) or Network File System (NFS) protocols. Note that once ephemeral OS disks care provisioned, they cannot be resized. IOPS is the number of requests an application send to the storage disks per second, so for an I/O size of 1024 KB and an throughput of 200MB/s results in an IOPS of 200
Azure Queue; used to store a large number of messages between application components
Azure Table; it store non-relational structure data, also known as structured no-SQL data, in the cloud
Data Redundancy; in Azure you have a minimum of 3 copies, this is an automatic process invisible to the end user. You can improve this is you like and provide a higher data redundancy by choosing options like below; all of them including 3 copies per region, meaning that if you choose multi-region you will have 6 copies of the data, 3 in the primary zone and 3 in the secondary zone:
- Locally Redundant Storage (LRS); have 3 copies in a physical location within a region; use a single-region and a single datacenter. This has 3 copies of the data but in a single datacenter. Premium data storage Page Blobs only supports LRS
- Zone-Redundant Storage (ZRS); have 3 copies across zones within a region; uses a single-region, meaning that there is no geographical protection, but the data is stored in at least 3 datacenters but all within the same region
- Geo-Redundant Storage (GRS); is like LRS but with a primary and secondary zone. This is multi-region, having 3 copies in the same datacenter, with the benefit of having the same copy in 2 different regions; in this scenario multiple nodes contain stored data, these nodes are in separate geographical locations and the data is read from both locations
- Read-Access Geo-Redundant Storage (RA-GRS); this option works as a failover, where data is available to read on the secondary location only is the primary fail
- Geo-Zone Redundant Storage (GZRS); is like ZRS in a primary region and LRS in a secondary region. This option is multi-region too, providing the maximum redundancy by having 3 copies in different zones in the primary region
Zone = Datacenter
Geo = Region


Primary Region Redundancy; indicates the Region that can be a single point of failure (LRS and ZRS), a large scale disaster may put down a Region
Tools for moving data: Azure comes with different way of moving data across your Azure VMs, like AZCopy (command-line utility), Azure Storage Explorer (GUI tool which you can download on your own computer) and Azure File Sync (sync files between Azure and on-prem file serves, handy for disaster scenarios where you want to use your data on the cloud just in case). For large scale migration with lots of data to migrate, you can use:
- Azure Data Box; in case you have slow bandwidth, the data is transfer to a box, and then from the box to your Storage Account or vice versa; Azure Data Box is an applicance that is best suited to transfer data larger than 40 TB. To use it, you first have to create the Data Box Edge Resource, then install it and assign an IP address of 192.168.100.5/24, activate it, and finally create the IoT Hub resource and configure the compute role. You can use the option in the Azure Portal to order a "Data Box Disk", where Microsoft will send you up to 5 SSDs disks of 7TB each; these disks are encrypted and Microsoft deletes the data after it uploads it. Data Box Heavy is a huge device that contains 1 Petabyte
- Data Box Disk can be use with only one storage account
- Data Box appliance and Data Box Heavy can be used with 10 storage accounts
- Azure Migrate; this is an appliance that discover on-prem or non-azure cloud system services, databases, VMs, etc to migrate them to Azure. Azure Migrate collects performance data and will help in recommending the size and compute of VMs that you might need in Azure
Azure Storage Reserve; is available for Azure Data Lake Storage Gen 2, and you must commit to a reservation of 1 year or more, if you do that Azure will give you a discount. The utilization percentage of Azure Reservations can be viewed on the Azure portal
Databases
"If you DATA doesn't exists in 3 different places, it really doesn't exist". Azure supports 3 types of data structure:
- Structured data, relational databases
- Semi-structure data, non-relational databases, non-sql where data is organised in tags and is all over the place
- Unstructured data, everything else, video files, etc
If you have all your data on-premisses, then all the security is on-you. You have to look after entrance, security door, CCTV, physical servers, etc. When you use Azure as IaaS you still have to worry about the security of the OS, networking, etc but not physical any-more, as Azure will look after that for you. With PaaS you still have to worry who can access that, while with SaaS all the security lies on Microsoft Azure, you deal plainly with the simple access, no "share responsibility" whatsoever
Cosmos DB; to create non-sql databases for modern app development with integration with open-source APIs, MongoDB and Cassandra. Cosmos DB is an example of PaaS. https://azure.microsoft.com/en-gb/services/cosmos-db/ Cosmos DB makes it easy to expand your data to other regions; Cosmos DB provide single digit milliseconds of latency across the world, providing infinite number of users. The big pitfall of Cosmos DB is....its price of course! Cosmos DB is a non-relational database, where data is stored in files
Azure SQL; for structured databases (sql), allows you to move your SQL data to the cloud. Azure SQL is use to manage Azure itself. Azure SQL supports up to 100 TB database in size. Azure SQL is composed of two components:
- Azure SQL Database, it most like the traditional SQL database
- Azure SQL Managed Instance; it meant to bridge the gap and help migrate on-prem DB to Azure
Here we got the main differences in between the two:

MySQL and PostgreSQL; open source databases, they are relational databases (built on relationship between tables), their format is also supported in Azure. MySQL use cases are web applications, e-commerce, mobile apps, digital marketing, finance management and gaming that must have low latency among others. PostgreSQL is the default DB for macOS, and some of the features it has are: extensions, horizontal scaling without impact on performance and fully managed like automated backup and patching. Governments, Financials and Manufacturing use PostgreSQL a lot due to its features
5. Authentication and Authorisation
Microsoft Entra ID (formaly known as Azure AD Service (AAD); you can't have an Azure account without an ADD service, every Azure account needs a first user and this user is the initial Microsoft Entra ID instance. A "tenant" represent an organisation in Azure Multiple subscriptions can be associated to a single tenant. Every Azure account will have an Azure AD service. A Entra ID can be a member of up to 500 tenants, and you can access the Microsoft Entra Admin Center portal in this link: https://aad.portal.azure.com
- Applications that do not use OAuth 2.0 are not able to authenticate to Entra ID Directory properly
- Microsoft Entra Identity Privilege Manager (PIM) assign privileges access to a resource thus reducing the change of a malicious actor getting access or an unauthorised user inadvertently impacting a sensitive resource
Azure Active Directory Domain Services (Azure AD DS); AD DS is a fully managed service, no need to configure any OS, though behind the screen there are 2 x DC for high availability. For AD DS you need to create a unique namespace/domain name (for example adds-nazaudy.com) totally separated from your internal domain name, and there is only one-way sync with Azure AD (Entra ID)

Azure AD Connect; it syncs the on-prem AD with the Azure AD
Zero Trust Security Model; ZT is a security methodology that assumes that every aspect of the network is vulnerable from attacks. Is a concept whether inside or outside the security boundary network, all users are assumed to be untrustworthy unless proven otherwise; your identity is the key to access the resources without the location (inside or outside building, the VPN, etc) like on the traditional model. You only give users the least level of permission that you can get away with
Multi-factor authentication; no excuses, 2FA is a must to access any resource nowadays, authenticate using your phone, fob, face, finger print, etc. MFA uses something you know (username+password) plus something you have (phone, fob, biometrics, etc). MFA; Multi Factor Authentication uses more than one thing to authenticate you. For the Azure account that manages Azure MFA is free of charge, but for everybody else... guess what, buy a licence
- Something you know, like a password or security question
- Something you posses, like your phone or an app on your phone
- Something you are, like finger print of facial recognition

Conditional Access Policies; they are "if" and "then" policies (access lists) in order to gain access to resources, you can do stuff like block sign-ins using legacy authentication protocols, grant access only from specific location, enforce MFA, etc. Conditional Access policies provide a way for an organisation to strengthen security access controls, it can be used to setup emergency access accounts (in case you get locked out of the Azure portal), evaluate your conditional access policies using the "What if" tool, and group applications having same requirements and then apply a single conditional access for those set of requirements
Passwordless Authentication; MFA is more secure but obviously is less convenient, with passwordless authentication you use the Microsoft Authentication App to generate an enter a code that is used as a password; FIDO2 Security key is another method, where you enter a USB that is used as a password
Microsoft Entra Password Hash Synchronicity; is an authentication method that allows users to use the same username/password that they have on-prem in the cloud, providing seamless SSO
Microsoft Entra pass-through; is an authentication method that uses a software agent to validate the on-prem credentials in the cloud, with this method users are authenticated by their AD, without any username/password
Federation authentication; this method is not natively supported by Entra ID, but if you use it with Password Hash Authentication, then this authentication method can allow you to have sign-in disaster recovery or leaked credential reports
Business2business accounts; you can invite external guest to Azure to provide business 2 business collaboration, effectively inviting external users into your internal environment without having to create an internal account for them
Azure Active Directory Seamless Single Sign-On; this is SSO for Azure
Azure B2B
- B2B Collaboration; Business to Business, allows you to share you Azure resources with another company Azure's stuff, this is like AD Federation services and Domains and Trusts, where users are listed in your Entra ID typically as guest users
- B2B Direct Connect; Establish a two-way trust with another Entra ID organisation and allows you to use chat, calls, file-sharing, app-sharing and Teams Connect shared channels
Azure B2C Business-to-Consumer; Business to Customers, allows you to share your Azure resources with customers on different organisations; with this method you can publish modern SaaS apps to consumers while using Entra ID for identity and access management
There are tons and tons of solutions in Azure, like for example:
IoT Central Hub; Internet of Things, provides data for millions of sensors. Internet Of Things Central is a SaaS solution that provide all pre-made components that you need
Azure Sphere; An all-in-one solution for IoT devices on Azure
Data Lake Analytics; where a data lake is a very large body of data; collecting data is easy, you just need to store it it, but to make sense of it and meaning is different, hence the following tools to extract meaningful content from the data are a business value: Data Lake Analytics, HDInsights (open sources supported)
Azure Databricks is an Apache spark-base analytics service; Apache Spark is a distributed cluster-computing framework; Databricks provides all the computer power
Azure Synapse Analytics (used to be called Azure SQL Data Warehouse), is used for reporting and data analysis, uses the Synapse SQL Language to manipulate the data in any way you need. The old Azure SQL Data Warehouse works with PowerBI
Machine Learning; this is the AI (Artificial Intelligence) of Azure where we allow the machines to take decisions for us. A model is a set of rules of how to use the data provided, the model finds patters based on the rules. Knowledge Mining use Azure Search to find existing insights in your data like file relationship, geography connections and more. The main tool to use machine learning in Azure is Machine Learning Studio, a pre-made modules for your project. The Machine Learning Service is a end-to-end service that uses AI almost anywhere in Azure; AI is about better products and better customer services
Azure Boot Service; this is machine learning Azure PaSS offering that lets you build boots for Q&A services, virtual assistants and more
Azure Cognitive Services; they provide vision to recognise images, decision to detect IoT anomalies and leverage data analytics and automatic speech-to-text transcription, for speaker identification and verification
DevOps; devops is the work between the development and the production of an app, code or feature. DevOps is about how developers, engineers and SysAdmins organise themselves and work as a team to deliver better products faster, and on that line Azure DevOps comes to helps with the following services
- Azure Boards (loved by project managers) that helps keep track of work tasks, timelines, issues, planning and much more
- Azure Pipelines; produce and test your software automatically and continuously; this service build and test code projects
- Azure Repos; store the code for your application
- Azure Test Plans; design tests of application to implement automatically
- Azure Artifacts; share applications and code libraries with other teams inside and outside your organisation
Azure DevTest Labs; it focuses on the environment to test and deploy the app, it allows you to track cost on VM resources, putting caps on the labs, as well as given you the option to create base Azure VM images and use Azure Resource Management (ARM) templates to quickly create new labs or modify existing ones
GitHub; is a code repository service for lots of big and small projects, it was bought by Microsoft in 2018. GitHub is well known for hosting open-source communities, being Microsoft one of its biggest users
GitHub Actions; is very similar to Azure pipeline, in which it is use to build, test and publish code
Hands-on with AI: use this Microsoft AI link to find out what AI can do for you: https://aidemos.microsoft.com/
The official link of Azure services when doing Microsoft free training is linked here:
Azure Site Recovery; keeps corporate workloads and apps up and running when planned and unplanned outages occur; ASR helps orchestrate replication, failover and recovery of workloads an apps so that they are available in a secondary location if the primary one fails
Defense in Depth; having a single security measure is....never enough! On chess, not only the queen defense the king, but also the pawns, bishop, knight, etc. The same thing goes for Azure and on-prem, you need to build up several layers of defense, these layers are: Physical >> Identity and Access >> Perimeter >> Network >> Compute (databases) >> Gateways and Firewall >> Data (ensure it is encrypted). Castles are wall, moats to prevent digging behind the walls, archers in the walls, etc, so when you think of Defence in Depth, think of castles
DDoS Protection Service; in 2012 60GB of traffic per seconds was sent on a DDoS attack in 6 banks, CloudFlare had similar attack in 2014 with 400GB of traffic per second, and GitHub suffered the same in 2018 with 1.35TB a second. The Distributed (meaning it comes from different sources) Denial of Service (DDoS) attack is the most fearful attack to suffer on the web
Network Security Group (NSG); are personal resource firewall that attach to virtual network, subnet or network interface. An extension of NGS is an Application Security Group that focus on securing an application rather than an IP endpoint
Private Endpoints; they are publicly reachable PaaS services, a good example of this is an Azure Storage (public endpoint) that is accessible your your on-prem VM, in order to secure this endpoints we use these methods:
Service Endpoint; you connect to the resource via the Azure subnet, Microsoft private backbone, hence not going through the public Internet, in other words, you privately connect VNet subnet to Azure PaaS services. The limitation of Service Endpoints is that it secures only VNet Azure access (not on-prem, meaning that on-prem must still use access over a Public IP), and its settings apply to the entire VNet and not to a single storage account if we need
Private Endpoint; acts as a managed network interface and is "better" than service endpoint, they use a private IP address (cannot be public) from the Azure virtual network and can be used for the following Azure services:
- Azure Storage
- Azure Cosmos DB
- Azure SQL Database
- A service using Private Link
Microsoft Managed Desktop (MMD); it is the MDM solution from Microsoft, it reduces crashes and boot time on devices, almost double battery time and when using with Enterprise State Roaming, users have the same experience when they sign in with different devices
Microsoft Defender for Cloud; a console where you get alerts, policy and compliance metrics, secure scores to visualise the strength of your security, etc. This console integrates with other cloud provides (but for that Azure Arc is required). To setup Defender for Cloud you need to define your policies, protect resources and response to any security alerts if any. The word "hygiene" is used in this context to tag the security weakness and best practices of the resources. Note that Defender for Cloud does not protect ACI (Azure Container Instances) but it does protect Kubernetes Cluster, containers that are VMs running Docker and Azure Container Registries (ACRs)
Microsoft Defender for Identity (formerly known as Advanced Treat Protection - ATP); a cloud-based security solution that identifies and detect compromised systems and identities as well as malicious insider actions. This solution is locate in https://portal.atp.azure.com/ and to access it you need to be a member of Microsoft Defender for Identity, the Azure AD security group. This contain an ATP Sensor that you install on your ADs and then send the data back to the ATP Portal, from where you can analyse al the security events. Microsoft Defender for Identity monitor users, create a baseline behaviour for them and suggest changes to conform with security best practices in order to reduce risks
Cyber-Attack Kill Chain; is a methodology used by hackers that follow: reconnaissance (search for IPs, info, etc), Brute Force and increasing Privileges
Azure Key Vault; this is a centralised cloud service where you lock your private keys, your passwords, certificates, tokens, API keys, etc. These are the two main ways to encrypt data on Azure:
- Storage Service Encryption (SSE), it encrypts the data before it is stored and decrypts it before it is retrieved, meaning that it is transparent to you; it is automatic and enabled by default on Blob, Managed disks, Queue storage and Azure Files
- Client-side Encryption; the data is already encrypts it by the client before Azure access it, this method implies that you store your private key on the Azure Key Vault
Azure Information Protection (AIP); companies need to share documents, emails and data outside of the company network. AIP is used to classify assets and apply tags and labels to contents, hence protecting files that are transfer between companies
Azure Sentinel; is a security information and event management (SIEM) tool, that works by first collecting the data from services (logs, dns, etc), then it does aggregation and normalisation of that data, and finally analysis and treat detection upon which actions can be taken. Some of the benefits and features of Azure Sentinel are: behavioural analytics, AWS integration and cloud scale meaning large companies use it
Azure Dedicated Host; in case you need to compliance with your company and run some VMs with specific hardware, etc, you can use Azure Dedicated Hosts, meaning you get control of the entire physical server on Azure without any other 'foreign' VMs but yours running on that host. The only issue with this is that, of course, it is expensive to provide hardware isolation at the physical level
Azure Security Center; it checks that you are doing the things right, monitoring that your settings for security are correct. Azure also uses machine learning to scan your machine for potential malware (Azure Defender) as well for any kind of attacks, if you enable those features ($$), of course
Azure Network Security group is a stateless firewall (analyses only traffic by port) while the Azure Firewall is a stateful firewall (analyses traffic end-to-end)
Azure address machine authentication in two ways:
- Service Principal, identity used by a service or application, most likely the credentials are stored on the code
- Managed Identity, a bit more secure as the credentials are automated by Microsoft, all you got to do is just enable/disable the access as needed. No security sensitivity information is stored in any code whatsoever
Azure Disk Encryption (ADE) is for the VMs data disk and that you have to turn it on
Transparent Data Encryption (TDE) is use to back up databases and log files at rest
Just a bit of theory, in IT we have to types of encryption:
- Symmetric; uses the same key for encrypt it and decrypt it
- Asymmetric; uses different keys, a public to encrypt it and a private key to decrypt the message
Azure Information Protection (AiP), a purchased add-on solution that helps you classify and protect your office documents and emails
Governance; set of policies to ensure Azure resources are in compliance with the policies, the example is a rocket launcher where sysadmin, devops, engineers, etc, all working together towards a goal guided by the Governance instead of each individual or group doing whatever they want
Compliance; companies in EU must comply with GDPR and other IT regulations
- General Data Protection Regulation (GDPR) main objective is to protect the individual by given them control of the personal data, instead of the company owning it; companies need to provide tools in place for the customer to control its own data
- ISO Standard; is an organization that creates different International Standard for Organisation (ISO) to normalise quality control and satisfaction. The most common ISO is 9001:2008
- NIST: National Institute of Standard and Technology focuses purely in providing compliance for Federal US Regulations
Azure Government; it uses the same underlying technologies as Azure and contains only Bring your Own License (BYOL) and Pay-As-You-Go (payGo) images of products; note that Azure Pipelines service is not available with the Azure Government offering
Cloud Adoption Framework; is use by the Governance to make a smooth transaction to the cloud
Management Groups; is a layer on top of subscriptions where you can managed them if you have more than one
RBAC (Role-Based Access Control); this is similar to the access list in NFTS, give the bare minimum permission that you an get away with. RBAC is the area where you configure the set of permissions and roles that users can be a member of to access Azure Services. Privilege Identity Manager (PIM), is an add-on to RBAC, a paid-for offering that makes sure of all the roles are all correct. RBAC works on the principles of Who, What and Where:
- Who; the security principal that needs the access
- What; the role assigned to the security principal
- Where; the permission given to the resource
RBAC are waterfall populated, meaning that if you assign a role to a subscription, all the resources inside that subscription will inherit them. Scope for Azure RBAC can be specified at multiple levels (Management Group, Subscriptions, Resource Group and Resource), and remember that RBAC information can be accessed in the Azure Portal of course but also in Azure CLI, Azure Powershell, Azure Resource Manager (ARM) templates and REST API. With RBAC, the more restrictive role that you apply will NOT have effect is above you have assigned a more wider permission
You access RBAC via the "Access Control (IAM)" option in the Azure Portal
Locks; they can de assigned to a subscription, resource group or resources
Azure Blueprints; are templates and artifacts where you can find rules and regulations, policies and sample of common regulations and highlights,; the blueprint templates are for compliance, for creating standard Azure environments and resources that adhere to a standard set of requirements, they are like ARM Templates, RBAC roles (Role-Based Access Control), policies, resources groups, etc. Blueprints basically put the creation of a new company in a JSON file, while ARM Templates puts the infrastructure on a JSON
The workflow of Azure Blueprint is Create >> Publish >> Assign.
Unlike ARM templates, Azure Blueprints retain a connection between the blueprint and what was deployed from it, and this allows for tracking an auditing
Azure Advisor; is a tool that helps you ensure High Availability and efficiency of your resources, it can help you and even fix problems for you in some occasions. Azure Advisor for Security Assistance is part of the Security Center. Azure Advisor Score is a sub-feature of Azure Advisor that help users asses how well they are following the guidelines of Azure Advisor
Azure Monitor; collects and analyse the health of your resources based on telemetry (events), you can also send to "Monitor" your data from the on-prem infrastructure as well as from other cloud-services like AWS. VM telemetry (data of sensors) is feed constantly into Azure Monitor, even on-prem VMs can be configure to send their telemetry data to Azure Monitor with the goal to maximise performance, availability and identify issues
- Azure Monitor Alerts; give you notifications of misbehaving in your VMs (unresponsive, high CPU usage, application latency over 500ms, etc). Your first create an alert rule with the condition and then specify the severity you wish, 1 for error, 2 for warning and 3 for informational. An email can be sent to a group using Azure Monitor and action can be configure for automation like triggering workflows depending on the condition of the rule, etc
- Application Insights; this is a feature inside Azure Monitor that gives you performance metrics, potential bottlenecks and more for your web base applications only; you can use this for app services in non-Azure resources also, in other words for web apps not hosted in Azure. Application Insights typical scenarios are to find performance bottlenecks in the web application, to discover how users are using the website and to detect performance anomalies automatically

Log Analytics; stores and queries the data to gain valuable insights, like VM disk size, VPN connection logs, network security, long term analysis. You can create queries using the Kusto Query Language (KQL) to ask the logs or choose some of the pre-built queries, this is similar to SQL queries; you can also combine metrics for complex queries. Azure Log Analytics can collect data from on-prem and store it on a single workspace
Azure Service Health; a tool to check how healthy Azure is and to see a history of previously incidents or downtimes of Azure, of course most of the time it would be working just fine, like on this screenshot:

Azure Service Health is a free service that you should use with any resource that you create; it will send Custom Alerts and provide Real-Time Tracking of how the issue is being solved as well as a Report of the root cause once all is up and running again, you can even integrate with ServiceNow using a webhook
Azure Trust Center; a gigantic resource or hub of information to prove that you can trust Microsoft with your infrastructure and data https://www.microsoft.com/en-gb/trust-center Note that Azure is K-ISMS certified, a certification designed to ensure the security and privacy of data in the Korean region. Azure Trust Center is built on four foundational principles of trust:
- Security; keep customer's data secure
- Privacy; how customers are in control of their data
- Compliance; comprehensive list of compliance offerings and solutions
- Transparency; being transparent about how Microsoft use customer's data
Service Trust Portal; another portal from Microsoft to show you how good they are at keeping and auditing your data, it contains a tool called "Compliance Management" that tell you if you're compliance with standards and data regulations: https://servicetrust.microsoft.com/ComplianceManager/V3 They audit their own performance and tell you that Azure complies with more standards than any other cloud provider. If an Azure tenant is deactivated, Microsoft permanently deletes all data for the tenant in the Service Trust Portal within 24 hours of the deactivation
Azure Compliance Manager; it gives you recommendation for ensuring compliance with GDPR, ISO, NIST and others. This extension comes with a Secure Storage area where you can upload secure documents for compliance if needed. The Azure Government Cloud is an area of the US government that ensure its datacenter and compliance with US federal laws. If you want to use Azure in China, you have to use the The China Region, which ensure it complies with China's laws and applicable legislation, where all data and datacenters are within China. If you choose to use Azure services in China, you must sign an Online Service Premium Agreement (OSPA) with 21Vianet, a company operated by Shanghai Blue Cloud Technology
Azure Arc; it provides a centralised governance and management of the resources (Azure, on-prem, AWS, etc) into a single location as to reduce the management overhead; it manages azure and non-azure resources as if they were in Azure. Azure Arc clarifies governance and management by delivering multi-cloud services and on-premises management platforms
Azure Purview; is a governance service that can help you manage data on-prem, in the Azure cloud and also in SaaS. Microsoft Purview creates a data landscape map containing data classification and end-to-end data lineage

Azure Policy; a service in Azure where you can define, assign and manage standards for the usage of resources in your environment, this is where you'll go if you want to allow let's say the Engineers team to have the ability to create their own VMs, with limitations. You can create policies to force the version of Windows to use, if https will be enforced, etc
- Policy Definition, is the first thing you need to create, it defines the action to take, which could be deny, disable, append, audit, deploy, etc. The Policy Definition is on JSON format
- Policy Assignment, you assign the Policy Definition to create a scope, you can assign to a subscription, resource or group
Azure Policy also audit settings inside a VM by using the Microsoft Desired State configuration v2 utility; VMs are deemed as non-compliant if they are not logging into a specific workspace of Log Analytics
Initiative Definition; a group of policies definitions that can be used as a common overarching goal; they can be assigned either to a management group or to a subscription. With Initiative Definition you have many policies but only do a single assignment, thus saving time and reducing management complexity and redundancy
The Cloud will save you money, but only if you make the right decisions, to save cost be aware of the followings
- the meters that you get charge for
- the VNet peering across regions
- plan your resources, you'll save if you can reserve
- consider other regions, some of them are cheaper than you preferred region and not that far out
Subscriptions: This is the core heart of Azure, subscriptions: nothing works without a subscription. Every single resource in Azure must belong to a subscription, they are billing entities. Any Azure account can have multiple subscriptions, useful when some departments within an organisation pay for what they consume, that way you monitor billing and usage of data granularly. The Billing Admin role manages the subscriptions in Azure, the payments are made within 30 to 90 days. This is what happens when you add a subscription to a Microsoft Entra ID tenant:
- Users with RBAC role lose their access
- Service administrators and co-administrator lose their access
- Existing key vaults are inaccessible until the key vault tenant ID is changed
- Managed Identities for resources such a Virtual Machines or Logic Apps must be re-enable or re-created
- The registered Azure Stack must be re-registered after adding a subscription to an AD tenant
- Multiple subscriptions can trust the same MS Entra ID, but each subscription can only trust a single directory
- Subscription help customers monitor the billing and usage of data granularly
- Subscriptions can be transferred to another country (a process called cross-country) but you have to contact Microsoft support for help, they just cannot be performed in the Azure portal
Groups Subscriptions; good to have them if when you have many subscriptions, you can group them into groups
Cost Analysis: use the Cost Alerts option too, to send alerts. You can use the "Spot VM Usage", an opportunistic method to save up to 90% of the cost of your VM, by using unused capacity of Azure, but be aware of "not to put any critical production processes on a Spot VM" because Microsoft, at any time, may ask for the processing power back; the VM can be evicted at any time
- Pricing Factors; calculating the Azure cost of a mature infrastructure is almost impossible, those to be consider are Resource Size, Resource Type, Location and Bandwidth of the Resource
- Billing Zones; Azure has 3 billing zone; the transfer of data between zones (ingress data-in) is always free, but if your data have to transfer between different billing zones (egress data-out) you got to pay for it
- Azure has a cost calculator to give you an "estimated", and where you can setup quotes to later export. The TOC can also be calculated
Azure Cost Management; best practice is to use "tags", non-functional label that you attach to a resource or resource group, having as many tags as you like, this helps you identify the roles of the resources. Each tag can represent a department or a project, and have a value to it. Invoice Manager is a role available for Cost Management for customers with a Microsoft Customer Agreement
- Pay-As-You-Go; is the consumption-based model, is not the cheaper subscription model, paying for month only for what you use; however, it would be cheaper if you can commit to a year of Azure usage
- Fixed Price Model; you are charged for the instances you have procured, and whether you use them or not, you must pay for the fixed price
- Reserve Instances in VM, where you commit for 1 to 3 years, come with a 70% discount, this also applies to Azure SQL (save of 80%), Cosmos DB (65%), Synapse Analytics (65%) and Redis Cache (save up to 55%). You can cancel your subscription at any time
- Azure Hybrid Benefit; this model allows you to use your existing on-prem licensing in Azure, eligible licenses are SQL Server and Windows Server with an active Software Assurance

Azure costs; the following are tips for managing the costs associated with your Azure subscription
- Azure costs can be filtered by the tags associated to resources and services
- Invoice Manager is a role that is available for Cost Managements but for customers with a Microsoft Customer Agreement
- AWS Cost and Usage report can be integrated with Azure Cost Management to analyse the AWS costs in the Azure portal
Azure Advisor; it gives you recommendations to safe money. You can also use the Azure Pricing Calculator to find out what you want: https://azure.microsoft.com/en-gb/pricing/calculator/
Price Plans; you have the pay-as-you-go (no long-term commitments or upfront payments), the Reservations (give you discount by purchasing a 1 or 3 years reservation) and these other app services (also called web tiers), where you commit per hour in the price https://azure.microsoft.com/en-us/pricing/details/app-service/windows/
- Free and Shared Plan; only 1GB of RAM and 1GB of storage, not supported for production workloads
- App Service Basic Plan; 10GB of storage
- App Service Premium Plan; 250GB of storage
- App Service Environment Plan; 1TB of storage
- App Service Domain; register your domain with Azure for $12 a year
- App Service Certificates; but an SSL for $70 dollars a year
Azure Pricing Calculator; find out how much you would pay before moving your stuff to the cloud by using this tool https://azure.microsoft.com/en-gb/pricing/calculator/
Total Cost of Ownership (TCO); lets you estimate the cost of migrating your workloads to Azure, and any savings that you could make https://azure.microsoft.com/en-gb/pricing/tco/calculator/
After you move your servers and workloads to the cloud, you can use these two tools to further optimise the costings, so we don't waste resources:
- Azure Advisor, also called just "Advisor", it gives you recommendation after a 14-days of usage to see if you actually need to downsize some VMs that were over specs
- Cost Management and Billing Service
If you buy Visual Studio you might be entitle to free Azure credit. Spending Limit is when you have spent all your credit and Azure then shuts down all your stuff
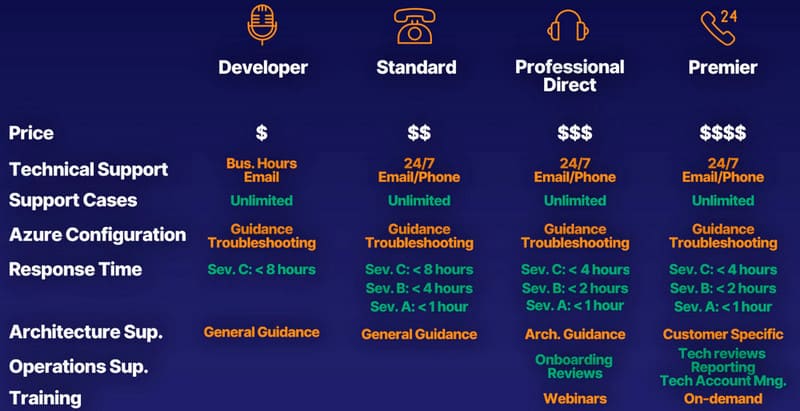
To provide support for Azure, Microsoft offers different plans to which you can subscribe to Microsoft Support plans, which are:
- Basic; it's free and includes all the free features
- Developer, Standard, Professional Direct and Premier. All the them can be signed up online except Premier, for which you have to contact Microsoft
All supported plans include "free" features like 24/7 access to billing and subscription support, online self-help, forums to ask other Azure users about issues, Azure Advisor and access to Service Health. the plans are listed here https://azure.microsoft.com/en-us/support/plans/
Tickets; A ticket is a support entity with a unique identifier number which is use as a single reference to an issue. You can submit tickets through the Azure portal, and Microsoft will attend your ticket on a time frame that depends on the support level you have
Channels; you can also get support by other different channels like Azure Documentation, Forums as well as Social Media
Knowledge Center; this is the gigantic documentation for Azure, where you can search for solutions (though you cannot ask new questions)
Service Level Agreement; the SLAs for Azure give you confidence that the services will be up and running (uptime and reliability); they are a contract with Microsoft and normally each product has an associated SLA agreement, they can be complex and they are mandatory for every Azure account. While you cannot choose an SLA, you can improve the value of it by purchasing a backup of a given VM, etc
Service Lifecycle; in Azure some services or features come first as a "Preview", which can be Private or Public; there after the service/feature goes into "General Availability", which is deployed in a rolling basis
Curious notes about Azure:
- Azure Germany offers a separate instance of Azure services from within German datacenter, and due to data privacy, only EU-based support staff provide technical support for Azure Germany's customers; the datacenters are only in Frankfurt and Magdeburg, thus ensuring all customer's German data remain in Germany

- Azure will not charge you for upload (they are already charging for space, anyway), but they indeed will charge you for any bandwidth of data leaving their datacener, for what you download from them https://azure.microsoft.com/en-gb/pricing/details/bandwidth/
- Enterprise Subscription model: you pay directly to Microsoft, most likely annually
- Cloud Solution Provider; you pay a 3rd party company who in return pay to Microsoft
London, May 2024
References
- https://medium.com/devops-cloud-it-career/why-did-i-take-the-microsoft-az-900-exam-1ef8fa5405a
- https://www.linkedin.com/pulse/exam-az-900-microsoft-azure-fundamentals-study-guide-jason-zandri/
- https://thecomputerperson.wordpress.com/2015/10/30/signing-up-to-microsoft-azure-and-avoiding-the-sorry-voip-phone-number-is-not-allowed-restriction/
- https://www.itexams.com/exam/AZ-900?
Old stuff, most likely no longer valid:
Azure Data Lake Storage Gen2; use for Big Data Analytics, you upload your data and then Azure analyses it. This seats on top of Azure Blob service; Data Lake include all of the capabilities required to make it easy for developers, data scientists and analysts to store data of nay size and shape, and at any speed, it works with Power BI too!
Azure Queue; to store a large number of messages, it helps out app to off load messages on their behalf
Power Apps, it lets you quickly build business applications with little or no code, allowing organisations to create websites which can be shared with external users through logon providers of their choice like Linkedin, Microsoft Account or other commercial login providers
Azure Traffic Manager; allows by the grace of DNS to put your resources as close of your customers as possible, avoiding in that way high latency and providing the best performance, but relies on replication (obviously) and it could expensive that is probably why Azure has an alternative to reduce the latency called CND:

Comments powered by CComment