Lab Setup for Microsoft Exam 70-640
This lab setup for Microsoft Exam 70-640- Windows Server 2008 Active Directory Configuring will prepare you for the exam in the following topics of the Windows Server 2008 R2 Operating System:
- Configuring Domain Name System (DNS) for Active Directory - 18%
- Configuring the Active Directory infrastructure - 17%
- Configuring Active Directory roles and services - 14%
- Creating and maintaining Active Directory object - 18%
- Maintaining the Active Directory Environment - 18%
- Configuring Active Directory Certificate Services - 15%
This time around I decided to use VMware instead of Hyper-V as the virtualisation technology on which to run the needed VMs for this lab. So go ahead and setup a couple of VMs, one to run ESXi 6 and the other FreeNAS, nothing fancy here, we're just gonna connect them through plain NFS
Hands on: Get DNS, Forest Root Domain Controller (FRDC) and deploy your test network
First of all, create our Hyper-V 70-642 VM and install on it the Hyper-V free version core edition from Microsoft, configuring that VM with the hard drives mentioned here. Once you got that done, copy the parent hard drives from the 70-643 VM to the 70-642 VM, and this is it, you're ready to start creating VM for this exam lab hands-on
Compact the parent disk if you like, but don't forget to set them read-only before creating additional VMs
1. Create a new VM called "DC01", and then create a differencing disk for it from the parent disk
2. Once you create the domain for our exam (ms642.internal), logon to our Hyper-V manager and add the host to the domain, then configure the "Automatic Start Action" of the VM to always start with the host, in order to provide authentication for it
3. Using Remote Desktop Connection Manager (version 2.7 here is the download: https://www.microsoft.com/en-gb/download/details.aspx?id=44989), create an .rdg file for our exam and ensure the "Drives" local resource are selected under the appropriate tab, given us access to our main computer where we got all the goodies downloaded and ready to go
4. On our DC, install the feature Remote Server Administrative Tools > "Hyper-V Tools" so we can manage our host from there
5.- Backup the "Default Domain Policy" GPO that we created on the 70-643 tutorial exam and import them into our DC01 for 70-642
6.- We would want to see a full map of the network regardless of the connection, so Turn On Network Mapping on Domain and Public Networks by modifying both entries of the Link Layer Topology Discovery (LLTD) the Discovery and the Responder found in Computer Configuration\Administrative Templates\Network\Link-Layer Topology Discovery
Remember that for a computer running XP you'd need to install the LLTD Responder on that computer
Remember that when you disable File Sharing on the profiles, you're also disabling the ICMP (Internet Control Message Protocol) meaning that the utilities part of this protocol - ping, tracert and pathping - will not work either
Remember to press the ALT key in order to view the menu and access the "Advanced Setting and Bindings" found under the ncpa.cpl or control net connections window
7. Now that we have done all this, have a look at the configuration we need to create for this test lab:
To achieve the above, create initially two additional private networks on our HyperV, call them "London" and "Chicago", and add the rest as you go along and progress with the lab
Then on the VMs that function as routers, add Roles > Network Policy and Access Services > Routing and Remote Access Services > and check both Remote Access Service and Routing. Once this is completed, add the RipV2 protocol on all the RRAS console and add also the relevant interfaces for routing
And finally issue the route print command on your MgmtPC so that packets going to either 192.168.50.0/24 or 172.23.50/24 are sent to your default gateway 10.10.10.254, the LAN connected to External on our Router1 VM
Have fun reading all this ;-) :
Stuff that is good to know about Domain Name Service (DNS)
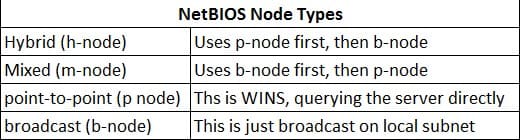
There are 3 ways that 2008 can get name resolution done: DNS , Link Local Multicast Name Resolution (LLMNR) and NetBIOS, these two are used in workgroups only and can resolve within the local subnet only; LLMNR is compatible with IPv6, but NetBIOS is not
To reduce zone transfer traffic when using AD (replication); obviously have an AD integrated zone in both main and branch offices, AD replication is faster and more efficient than file-based replication, and remember that primary, secondary and stub-zones are file-based zones.
Zone transfers are pull operations; the primary sends a notification to the secondary whenever there is an update (check the "Notify" button under Zone Transfers) and then the secondary initiates a zone transfer from the primary.
Some of the lovely and useful commands that you can use to manage your DNS servers:
- dnscmd / clear cache
- dnscmd servername /createdirectorypartition FQDN
- dnscmd servername /enlistdirecotrypartition FQDN
- dnscmd /enumdirectorparitions
- dnsmd/ info
- dnscmd /zoneupdatefromds ;run this from an AD integrated zone to update the RODC and secondary servers
- dcdiag /test:replications
- repadmin /showreplroute
The DNS server role in Windows Server 2008 R2 contains 4 new features:
- Background zone loading
- IPv6 support
- Support for Read-Only Domain Controllers (RODC)
- Global Names; provide a single name resolution for large enterprises that do not contain a WINS server (you can create single name resources on the global name zones); for this type of zone to work it must be integrated on AD and all the SOA DCs of the forest must be running Windows Server 2008. To enable GlobalNames support run dnscmd . /config /enableglobalnamessupport 1 , it facilitates the resolution of single-label names in a large network
What type of zone to be deployed:
| What type of zone? | Improve Name Resolution? | Minimize zone transfer? | Keep an updated list of remote NS? |
| Root Zone (.) | The root zone (.) must be deleted before adding a forwarder DNS server or coditional forwarder zone | ||
| AD-integrated | YES | YES | YES |
| Primary Zone | YES | - | - |
| Secondary Zone | YES | Nope, the entire zone is copied periodically | YES |
| Stub zone | YES | YES | YES |
| Conditional Forwarding | YES | YES | Nope, only one DNS act as a bridge. A conditional forwarder just forward queries to a specific domain; use when you want two forest to talk to one another |
| Global Names zone | - | - | - |
| Delegation | Delegations can only be created in a parent domain for a child domain | ||
| Cache-only server | This is a DNS with no zones configure, only the root hints available; this kind of cache-only server is useful to deploy on branch locations where there is no technical expertise available, a cache server will improve resolution by caching the queries addressed to the main branch | ||
Stub Zones are often use to enable a parent zone like domain.com to keep an updated list of the name servers available in a delegated child zone, such as child.domain.com; it only contains those records necessary to identify the authoritative DNS servers for the master zone
With Standard zones you can configure only a single read-write (primary) copy of a zone data, all the other copies of it (secondary zones) are read-only. Unlike AD integrated zones, this primary zone represents a single point of failure
When you want to configure DNS servers at different locations and each location has a domain controller, creating an AD integrated zone is recommended because it reduces the load on network bandwidth
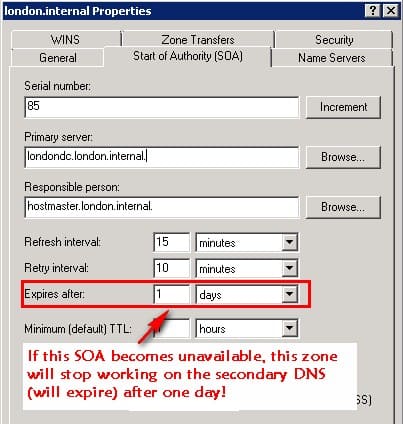
On the SOA record, the name of the primary server must end with a period, and the "expires after" value on that same SOA record determines the length of time that a secondary server, without any contact from its master, continue to answer queries from DNS clients and be authoritative
A Name Server (NS) record specifies a server that is authoritative for a given zone
To enable aging for a particular zone, you have to enable this feature both at the server level and at the zone level. Manually created records have a timestamp of zero (static) meaning that they will not be aged
- Scavenge non-refresh interval; during this time the server rejects a timespam refresh
- Scavenge refresh-interval; timestamps are accepted but resource records are not scavenged
- By default, with 7 days on each period, a dynamically registered resource record can be scavenged after 14 days. Remember that the refresh interval should always be bigger -greater - (or at the minimum equal) than the non-refresh interval
DNSSEC is a set of extensions of DNS, providing origin authentication of DNS data, data integrity and authentication denial of existence. To support DNSSEC (Domain Name System Security Extensions) you need to create the following resource records
- Signature (SIG) resource record
- Public Key (KEY) resource record, associated with the specific zone itself, not the DNS hosting the zone
- Next domain (NXT) resource record
Replication Scope; you can store a zone on the DomainDnsZones, the ForestDnsZones or a custom created zone; choose "To all domain controllers on this domain" for Windows 2000 compatibility, this last partition replicates to both DNSs and DCs
Talking about replication between sites: for each AD partition, only one DC on each site is designated as a bridgehead, and replication occurs only between those bridgeheads
A smart way of installing DNS on a server core server, is to install it first on a GUI server, then , on the last window, you have the option to export the settings to a .txt file that you can use to run it on the Server Core by executing: dcpromo /unattend:file.txt
If for some reason you're configuring a DNS server to be a root (.) server, delete the cache.dns file found in C:\Windows\System32\dns, that file contains the servers displayed on the Root Hints tab
Stuff you can do to learn DNS
On all DNS servers create a AD-integrated zone called "confidential", then add some dummy A records in there, then created an application directory particion on each DNS server by running dnscmd . /createdirectorypartition DNSpartition.confidential and store the zone on that partition, see how it replicates to the other DNS
Stuff that is good to know about Dynamic Host Control Protocol (DHCP)
When a computer running IPv6 starts up on a network, it can configure itself on two different ways:
- Stateless Configuration; the computer will ask the router for its network prefix (the router needs to support IPv6 stateless configuration), once the computer has the prefix, it will add it to its mac address (example: FD00:A000:BC12:0012:48d5:18e5:394c:c9ba) and will contact a DHCP for additional information like DNS, Gateway, etc
- Stateful Configuration; on this mode the computer will contact the DHCP server directly for IPv6 full configuration. If you don't have a router that supports IPv6 stateless configuration, you would need to use stateful mode. To configure this mode set the M flag to 1 by running netsh interface ipv6 nicName managedaddress=enable To obtain configuration settings, such as DNS server address, set also the O flag to 1 by executing netsh interface ipv6 nicName otherstateful=enable
To quickly find out the MAC address of a remote computer type getmac /s computerName | clip to copy to clipboard
NAT (Network Address Translation) is not used on IPv6
A reminder of the Private IP addressing used in IPv4:
- 10.0.0.0/8, running from 10.0.0.0 to 10.255.255.254
- 172.16.0.0/12 running from 172.16.0.0 to 172.31.255.254
- 192.168.0.0/16 running from 192.168.0.0 to 192.168.255.254
- 169.254.0.0/16 - the good old APIPA (Automatic Private IP Addressing)
To enable ICMP through the firewall, enable File Sharing in Network and Sharing Center
arp is both an utility and a protocol (Address Resolution Protocol) use to translate IPv4 to MAC addresses; issuing the command arp -a you'll see the IPv4-to-MAC table; IPv6 uses the protocol Neighbour Discovery (ND) to resolve IP-to-MAC, preventing the possibility of cache poisoning present in ARP
A subnet is a single broadcast domain, while a network could also be that (a single subnet) or a group of connected subnets
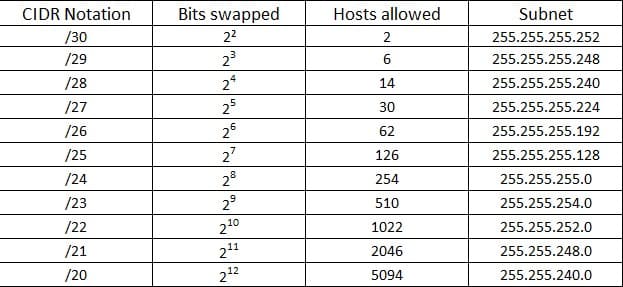
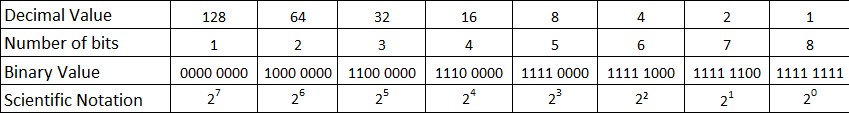
Some tips about IPv4 CIDR (Classless Inter-Domain Routing) notation here:
Stuff that is good to know about IPv6
Windows XP SP2 and earlier do not have IPv6 installed by default (but IPv6 is supported on XP SP1), to install it on them run the command netsh inferface ipv6 installOnce you install it, you need to configure Teredo on the network as well as enable Teredo for the Windows XP SP2 computers by running netsh interface ipv6 set teredo client; by the way these are some useful commands that you can issue on netsh:
- netsh interface ip set address "lan name" static "ip address" "network mask" ; assign an IPv4 to the specified lan
- netsh interface ip set address "lan name" dhcp ; configure the interface to use DHCP
- netsh interface ipv6 set address "lan name" "ipv6 address"; assing an IPv6 to the specified interface
- netsh interface ipv6 show interface ; display the IPv6 associated with each interface
IPv6 address mappings and some tips
- The loopback address is 0:0:0:0:0:0:0:1, equivalent to the 127.0.0.1 in IPv4, and can be denoted as ::1
- FD00:AB10:2B5C:B000::/8 site-local used when clients need to communicate to one another across an entire organisation
- FEC0:AB10:2B5C:B000::/10 are private addresses
- FE80:AB10:2B5c:B000::/64 are equivalent to APIPA on IPv4, the 169.254.0.0
Due to the different header format that IPv6 uses, routers need to be able to support it, in other words, be compatible with IPv6
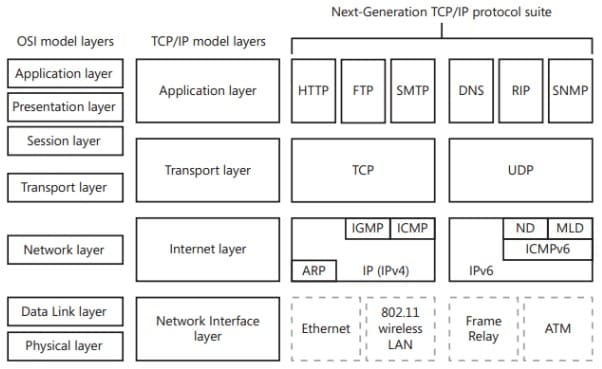
Unlike IPv4, IPv6 does not rely on network broadcasts; instead of broadcasts, IPv6 uses multicast or anycast transmission
To allow transaction from IPv4 to IPv6 there are four different technologies currently in use:
- Next Generation TCP/IP; this is the fact that IPv6 is installed alongside the IPv4 on Windows Vista and above
- Intra-Site Automatic Tunnel Addressing Protocol (ISATAP); encapsulates IPv4 inside IPv6 and performs like a NAT router; intended to use inside a private network
- 6to4; similar to ISATAP (IPv4 encapsulated in IPv6 packets) but intended for public network (the Internet); in addition it has the requirement that it needs 6to4 compatible routers
- Teredo; another tunnelling protocol that allow clients behind an IPv4 NAT to use IPv6 on the Internet; generally used when there are no other IPv6 protocol transition available. For Teredo to work an infrastructure needs to be setup, consisting on the clients (obviously), Teredo servers, Teredo relay and host-specific relay
To disable IPv6 transition protocols and give preference to IPv4, you can create a DWORD(32-bit) key called "DisabledComponents" inside HLM\System\CurrentControlSet\Service\tcpip6\Parameters and set its hexadecimal value to these settings depending of what you want to achieve:

IPv6 Addresses types; these are the types of IPv6 in comparison to the IPv4 addresses
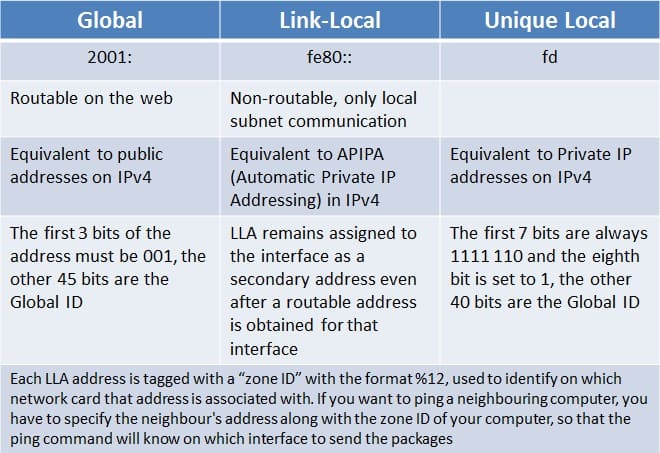
The zone ID of an LLA address %12 is used to identify the nic on which that address is associated
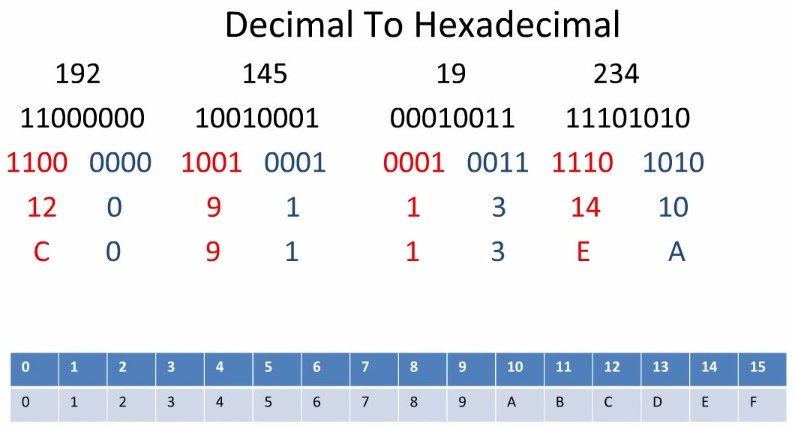
A hint-table-tip about the conversion IPv4 (decimal) to IPv6 (hexadecimal):
By default, you subnet the "fourth octet" on an IPv6 address, though you can borrow more bits from the host section if needed:
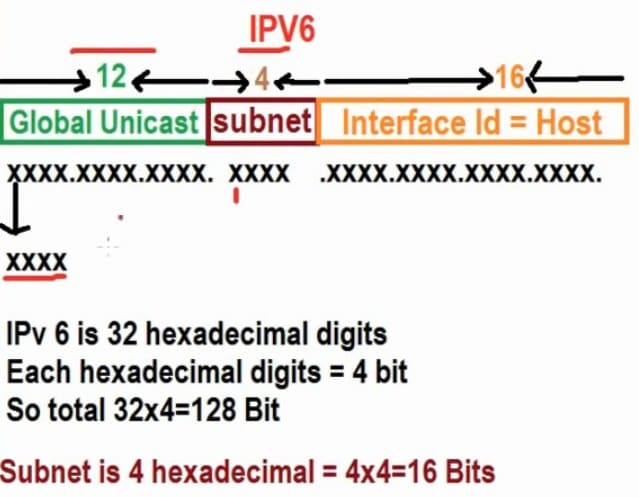
This is the terminology updated to IPv6: The network ID in IPv4 is called Prefix in IPv6, and by default consists on the first 64-bit of the address
The host ID in IPv4 is called Interface Identifier in IPv6, consisting on the remaining 64-bit
In an IPv6-only subnet without Network Discovery or DNS, you cannot ping a computer by name, connect to a computer by its UNC or see it listed in the Network window; this is because NetBIOS does not exist on an IPv6 network
To configure the router advertisements on IPv6 routers
Stuff that is good to know about Routing and Remote Access Server (RRAS) and NAT
There are three stages that make up a remote connection:
- Connection: making the physical connection, where encryption and protocols are negotiated, if the encryption or/and protocols do not match, the connection fails
- Authentication; identify who they are by the means of username/password/ IP Addresses/ Certificates / Smart cards, etc
- Authorisation: determine what they can access, by the means of IP filters or NTFS Permissions
- When troubleshooting, keep these stages in mind: has a connection occurred? has authentication occured? has authorization occurred? Break the problem always in smaller parts, how do you digest an elephant? steak by steak
Configure the IP filters for a VPN connection on the nic facing the outside world
RADIUS (Remote Authentication Dial-In User Service), this good old service centrilizes the famous triple A (AAA):
- Authentication
- Authorisation
- Accounting
Lovely commands that you can use to troubleshoot or managing routing:
- tracert; provides a quick response
- pathping; provides a more detailed and reliable analysis of network performance
- route -p add 192.168.10.0 mask 255.255.255.0 192.168.1.1 ; this sends all traffic for the 10 network to the 1.1 router
Windows maintains separate routing tables for IPv4 and IPv6; how do you decipher a routing table? here are some tips:
- The persistent router section displays any static routes that have been configured; non-persistent routes will be removed upon a reboot
- routes with the 0.0.0.0 indicate the default gateway
- router with all 255.255.255.255 are network interfaces can can be ignore
The key difference between pathping and tracert is that pathping computes accurate performance statistics over a period of time, while tracert sends only three packets to each router in the path and displays the latency for each of those three packets. Pahtping is similar to tracert except that pathping is intended to find links that are causing intermittent data loss, and since pathping shows the degree of packet loss, you can use it to pinpoint which routers might be causing network problems
If required you can configure the following three types of NATs:
- Cone NATs; store a mapping between an internal address-port and an external address-port in the NAT translation table
- Restricted NATs; store the same thing as the Cone NATs with the difference that they use either a specific source address or a specific source address-port
- Symmetric NATs; they map the same internal address-port to different external address-port
Stuff that is good to know about VPN and security protocols
Windows Vista and above do not longer support the good old fashing MS-CHAP v1
Windows Server 2008 acting as a VPN server can accept these protocols:
- PPTP provides simple Windows authentication
- L2TP, which is based on IPSec, requires client certificates for authentication and thus requires you to implement a PKI
- SSTP, supported only by Visa, 7 and Server 2008, provides VPN connectivity across proxy servers and firewalls
In regards to the protocols these are some things good to remember:
- L2TP/IPSec; it provides machine and user authentication (IPSec provides mutual machine authentication, data integrity, confidentiality and non-repudiation) before gaining access to the VPN server
- EAP-TLS (Extensive Authentication Protocol - Transport Layer Security); allows to secure the user credential information by using certificates, but does not ensure that both user+machine are authenticate before gaining access to the VPN server
VPN Reconnects via IKE2 (with both machine and user authentication) only supports Windows 7 and Windows Server 2008 R2
Stuff that is good to know about routing and IPSec
On a Windows Server 2008 environment we can implement IPSec in two ways:
- IPSec policies; by default they attempt to negotiate both authentication and encryption services
- IPSec Connection Security Rules; by default they do not encrypt data and attempt to negotiate only authentication services, providing only protection against spoofed data, altered data and replay attacks
On a Windows Server 2008 environment IPSec can work on two modes:
- Transport Mode; this is the default, using LT2P
- Tunnel Mode; LT2P is not use, and the packet is encapsulated by another header; tunnel mode is not support for remote access VPN
You create a Policy, that then contains a rule, that then contains a filter, that then has an action associated to that filter ;-)
Staff that is good to know about Direct Access
Direct Access allow clients to maintain a constant connectivity with intranet
- All clients must be running at least Windows 7 (XP and Vista do not support it)
- Enable IPv6 on all clients and servers
- Issue a computer certificate for IPSec authentication for the client computers
- Servers that will use Direct Access must be Windows Server 2008 R2 (must be R2, the Server 2008 is not supported) and have 2 nic, once for the Internet and one for the internal network
- DirectAccess: allow clients to maintain constant connectivity. IPv6 is required to provide end-t0-end addressing, allowing users to established an IPv6 tunnel to a DirectAccess server over an IPv4 internet. All clients that use DirectAccess must be running at least Windows 7. All servers that use DirectAccess must be running Windows Server 2008 R2 and must be domain members.
Staff that is good to know about Network Policy Server (NPS)
NPS cannot be configured via GPOs, but you can create NPS templates to transfer settings to other NPS servers; this is only available for Windows Server 2008 R2. These are the templates available:
- Shared Secrets
- Radius Clients
- Remote RADIUS Servers
- IP Filters
- Health Policies
- Remediation Server Groups
To support NAP (Network Access Protection) the NAP infrastructure must include a RRAS, DHCP and NPS server. The NPS server must be 2008 or 2008 R2. NAP clients must be running Vista or above, for XP there is a NAP client included on the XP SP3. DCs and PKIs server can run 2003 and above.
Staff that is good to know about Windows Firewall
You should enable Windows Firewall logging only as a troubleshooting technique, to do so right-click on the console Windows Firewall and Advance Security, and specify the logging for the profile that you want:
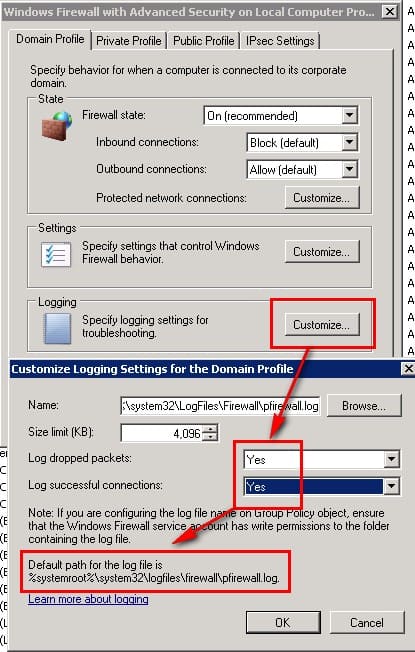
To find out what applications are using what ports run the command netstat > list.txt and examine the output, use the command in combination with the following switches:
- -a ; displays al connections and listening ports
- -n ; displays addresses and port number in numerical form
- -o ; displays the owning process ID associated with each connection
- -b ; displays the executable involved in creating each connection or listening ports
Staff that is good to know about BranchCache
BranchCache improves the performance of applications that use HTTP, HTTPS and the file sharing protocol of SMB by caching HTTP and SBM content on a server running Windows Server 2008 R2 with BranchCache enable. BranchCache can operate on two modes:
- Distributed Cache; best suited when a cached server is not available on the branch site. Windows 7 clients will cache content pulled from the server at the main and will send the content to other clients on a peer-to-peer architecture. For this to work TCP 80 and WS-Discovery traffic UDP 3702 must be open at the firewall
- Hosted Cache; in this mode a 2008 R2 server is installed at the branch with BranchCache feature installed. To enable clients to use this mode run netsh branchcache set service mode=HOSTEDCLIENT LOCATION=FQDN_of_branched_server on the clients once you have the feature installed on the server
Events subscriptions
To collect events from one computer to another, do the following:
- SRV01; the source, you need to run winrm quickconfig
- SRV02; the recepient, you need to run wecutil cs subscripton.xml command
- Add the recepient server to the local administrator group of the source server
- Finally, create a new subscription on the recipient server
Both of these services Windows Remote Management (WinRM) and Windows Event Collector (Wecsvs) must be running on both servers for the event subscription to work
Note the difference between the Windows Event Collector Service (wecsvc) and the Windows Event Collector Utility (wecutil)
Well-known and not that well-known ports
Here are just a few:
- Port 20 is used by FTP
- Port 21 is used by FTP
- Port 22 is used by Secure Shell (SSH)
- Port 47 is used for Point-to-Point Tunnelling Protocol (PPTP) over General Routing Encapsulation (GRE)
- Port 50 is used by Encapsulating Security Payload (ESP)
- Port 51 is used by Authentication Header (AH)
- Port 53 is used by DNS
- Port 67 is used by DHCP, enable it on WDS when the DHCP is on a different subnet
- Port 68 is used by DHCP client communication
- Port 69 is used by TFTP, must be open on a WDS server
- Port 135 is used by DHCP Manager communication
- Port 401 is used by an uninterruptible power supply (UPS)
- Port 500 is used by Internet Security Association and Key Management Protocol (ISAKMP)
- Port 546 is used by DHCP IPv6 client
- Port 547 is used by DHCP IPv6 server
- Port 587 is used by SMTP (System Mail Transfer Protocol) encrypted, outgoing mail
- Port 636 is used by Lightweight Directory Access Protocol (LDAP)
- Port 995 is used by POP3 encrypted, incoming mail
- Port 1701 is used by Layer 2 Tunnelling Protocol (L2TP)
- Port 1723 is used for PPTP control
- Port 1812 is used by RADIUS authentication messages UDP
- Port 1813 is used by RADIUS accounting messages UDP
- Port 4011 is used by PXE, must be open on a WDS server
Stuff that is good to know about other Stuff
Download Network Monitor 3.4 (the x64 version) from here: http://www.microsoft.com/en-us/download/details.aspx?id=4865 and capture some packets as you go along
Guide: Table of IP Addresses for this lab
| No | Server Name | IP Address | Roles and Features |
| 1 | Hyper-V | 10.10.10.30 | Host VMs for 70-642 exam, the VMs below |
| 2 | DC01 | 10.10.10.70 | AD Directory Services (+ DNS) AD Certificate Services |
| 3 | Router1 | 10.10.10.254 192.168.50.254 172.23.50.254 | LAN Routing |
| 4 | WSUS1 | 10.10.10.75 | WSUS |
| 5 | WSUS2 | 10.10.10.76 | WSUS downstream |
| 6 | LondonDC | 192.168.50.70 | AD Directory Services (+DNS) DHCP (192.168.50.100-120\24) Distributed File System (DFS) |
| 7 | LondonRRAS | 192.168.50.71 | NPS HRA - Heath Registration Authority |
| 8 | London1 | 192.168.50.100 | |
| 9 | ChicagoDC | 172.23.50.70 | AD Directory Services (+DNS) DHCP (172.73.50.100-120\16) Distributed File System (DFS) |
| 10 | ChicagoRRAS | 172.23.50.71 | |
| 11 | Chicago1 | 172.23.50.100 |
Excersice 1: Configure IPSec between London1 and Chicago1
First of all we'll configure the PKI (Public Key Infrastructure) for both domains, by visiting each DC and enabling the Auto-Enrollent so that clients can support EAP Authentication.
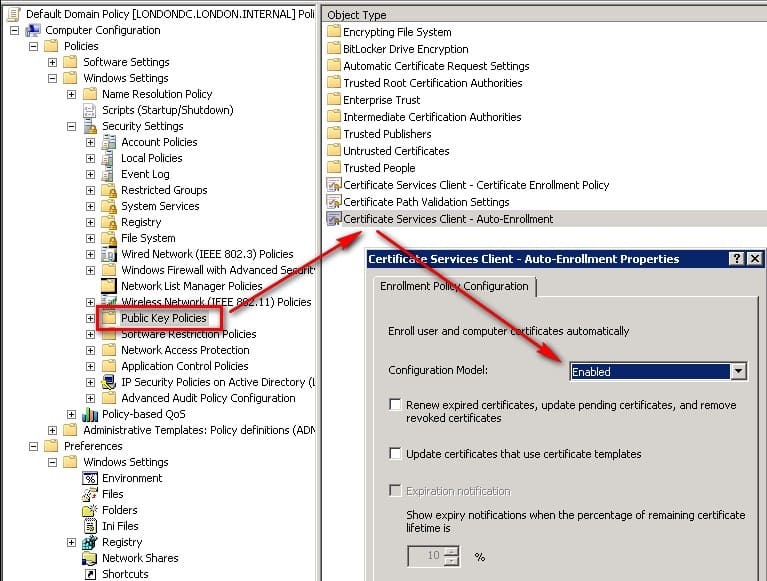
There are two ways in which we can secure the traffic between these two VMs: by configure individual rules to each server or by applying a policy to them
Excersive 2: Configure WSUS server, upstream and downstream
1.-Create a new VM called WSUS1 and download the Windows Server Update Services 3.0 SP2 from here: http://www.microsoft.com/en-gb/download/details.aspx?id=5216 Ensure that the roles "Application Server" and "Web Server (IIS)
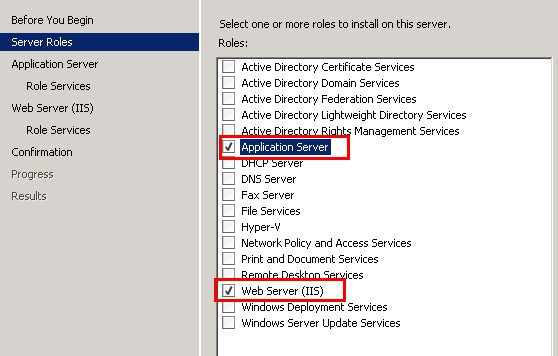
2. The following Role Services (found under Web Server IIS) are also needed for the operation of WSUS:
- Application Developement > ASP.NET
- Security > Windows Authentication
- Performance > Dynamic Content Compression
- Management Tools > IIS 6 Management Compatibility
In addition to the above you'll also need the "Microsoft Report Viewer 2008 Redistributable" that you can get from here: http://www.microsoft.com/en-gb/download/details.aspx?id=6576
3. Create another VM called WSUS2 and configure it to be the downstream server of the WSUS1. Once done that, modify the GPO on our Finance OU in the London DC and ensure that London1 computer is to get the updates from WSUS2, see how that works!
4.- The two main settings to configure are "Configure Automatic Updates" and "Specify intranet Microsoft update service location", after that you're good to go and the computer will show on the WSUS server
Stuff that is good to know about WSUS
If you configure the downstream server as a replica, you don't need to approve updated on it, they can be approved at the upstream
If you configure the downstream server as an autonomous server, you must manually approve updated on that server
Minimun space of 6GB to store the updates locally
By default the WSUS database is located at C:\WSUS\UpdateServicesDbFiles\SUSDB.mdf and it requires a minimun of 3Gb free space on the drive
Server-side targeting; manage the comptuers through the console in the WSUS server
Client-side targeting; need to create computer groups, then GPOs to add the computers to that groups and received updates
Troubleshooting errors: The Application Log should always be the first place you check when troubleshooting WSUS errors
- Check the logs under C:\Program Files\Update Services\LogFiles
- Examine the %SystemRoot%\WindowsUpdate.log from the client box to find out any problems with it
- Verify that clients can connect to http://wsus-name/idudent.cab ,they should be asked to save a file
- If using GPOs, run the Resultant Set of Policies Tool, rsop.msc to verify the configuration
- If you made a change, restart the Windows Update Service for the change to be effective, or run:
- net stop wuauserv
- net start wuauserv
To make Windows Update query the WSUS server run this command: wuauclt /a
Exercise 3: File Sharing, Printing and Monitoring. Configure DFS beween both domains
These are some of the tips regarding the above subjects
Microsoft Baseline Security Analiser is a wonderful tool that check for weakneses on the system: http://www.microsoft.com/en-gb/download/details.aspx?id=7558
In Network Monitor, a "capture filter" filter frames before they are captured (capture filter must be created before capturing data)
In Network Monitor, a "display filter" filter frames after they are captured.
To capture on P-Mode (promiscuos mode) using the command line, execute: NMCap /network * /DisableLocalOnly /capture /file filenam.cap
If you have enjoyed reading this article about Lab Setup for Microsoft Exam 70-640, you might enjoy this other one: https://www.nazaudy.com/lab-setup-for-microsoft-exam-70-642
19 August 2015
References
Unattended Installation of Active Directory Domain Services; great article from Tarek Majdalani: http://www.elmajdal.net/win2k8/unattended_installation_of_active_directory_domain_services.aspx
Use Network Mapping on Domains and Public Networks; with thanks to Ed Bott, Carl Siechert and Craig Stinson https://technet.microsoft.com/en-us/magazine/ee924643.aspx
Add New Virtual Network Interface to RRAS; credit to AnupamC for this tips about how to back up RRAS https://social.technet.microsoft.com/Forums/windowsserver/en-US/8cf4b67e-6d5a-4e6d-9ba3-4ef86dacbe33/add-new-virtual-network-interface-to-rras
Windows 7 / Windows Server 2008 R2: Distributed Scan Management; thanks to CC Hameed for this comprehensive article http://blogs.technet.com/b/askperf/archive/2009/10/11/windows-7-windows-server-2008-r2-distributed-scan-management.aspx
IPv6 Subnetting CCNA 5.0 - Video 3 part 1; congrats to okzbd for this great video (forget about the nasty comments, you're great!) https://www.youtube.com/watch?v=RotlraQnLpE
The Cable Guy - The DHCPv6 Protocol; huge thanks to Joseph Davies for his clear explanation on DHCPv6 https://technet.microsoft.com/en-gb/magazine/2007.03.cableguy.aspx
IPv6 Problems, how to disable it; great answer from Edoardo Benussi https://social.technet.microsoft.com/Forums/windowsserver/en-US/8f1e675c-662d-452f-90ab-bd3727de5927/ipv6-problems
Okay, to do this lab we are going to setup two Server Core 20085 R2 domain controllers with their respective RRAS server on two different location called London and Chicago.
1.-Starting with London, create from the "ParentCore.vhd" a VM called LondonDC and install DNS on it by running, by running this:
dism /online /enable-feature /featurename:DNS-Server-Core-Role2.-Then, open notepad on that server core and paste this text on it, save it as "LodonDC.txt", that will be our unattended installation; use the Clipboard > Type clipboard text and see how cool it goes
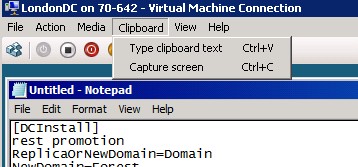
3.- If you are presented with the error "The referenced assembly is not installed on your system", that means that .net Framework 2.0 is not enable on the server, fix it by running this command:
dism /online /enable-feature /featurename:NetFx2-ServerCore-WOW64
London, 29 December 2017
Comments powered by CComment